OSINT Writeup — IEEE VICTORIS4 CTF Finals
Introduction
After a full 6 hours in the IEEE VICTORIS4 CTF finals phase, I’m happy to share my write-up for three OSINT challenges I created: two Investigations (Easy/Medium) and one Geo (Hard).
This is a step-by-step walkthrough aimed at beginners.
Domains of Deception
Description
Whispers spread across the net: a phantom domain-smith forging shadows of giants. His masterpiece? rnicrosoft[.]com — a false mirror of trust, luring the careless. One careless step led hunters to his trail.
Follow the traces. Unmask the trickster. Gather his secrets.
Flag parts:
⦁ First part (scammer name): the scammer’s real full name.
⦁ Second part (oldest domain): of the >16,390 domains registered under the scammer’s name, identify the oldest domain registration (domain string only, e.g. example[.]com).
⦁ Third part (leaks): how many data leaks (leaked datasets) were found associated with the scammer’s accounts? (a numeric count)
Bounus: If you recover a password from the leaked data, submit it as an optional fourth Bounus token.
Flag format:
IEEE{Real_Name,oldest.domain,Leakcount}
First, we need the Scammer's name so we open WHOIS Domain Lookup and search with the domain name, now we know who is the Registrant a.k.a. Scammer and also some extra useful info about him.
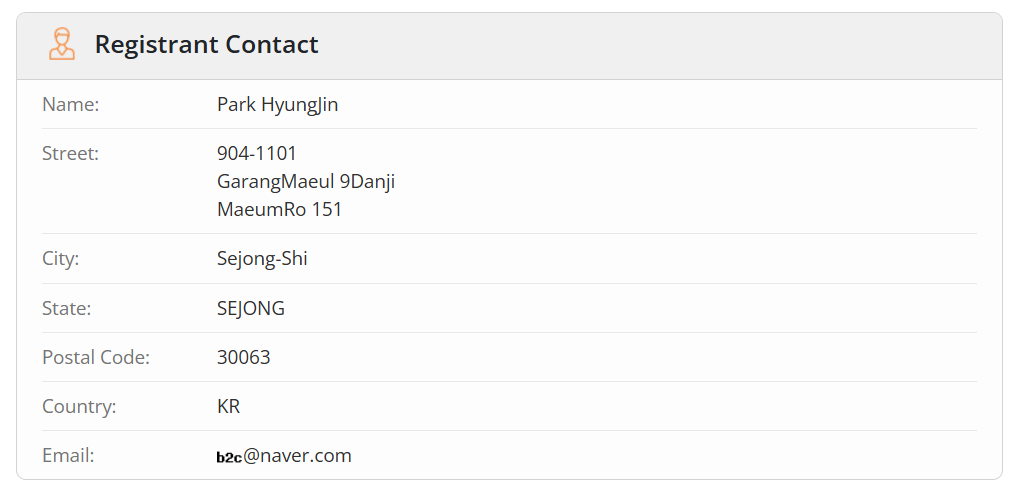
Now, we know that he has over 16,390 domains registered under his name,
with that much records, if we went to whoisology.com and searched with the Registrant name Park HyungJin, we will get a partial list of records, but those records aren’t in order and we will have to search for the Creation Date manually in all of them.
After some search, we find this website that offers the full list with a price of $25, it also shows only 100 records without price as a free trial, so we clarify our search filter like this:
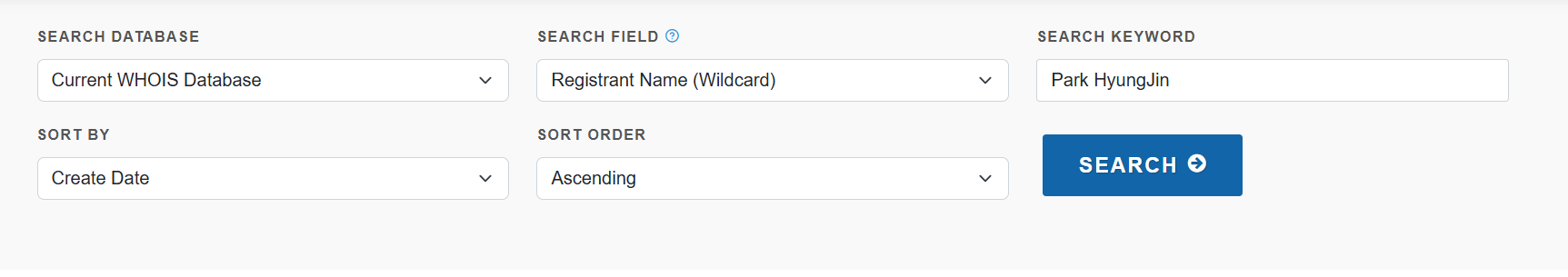
Now we get this result for the oldest 100 records:
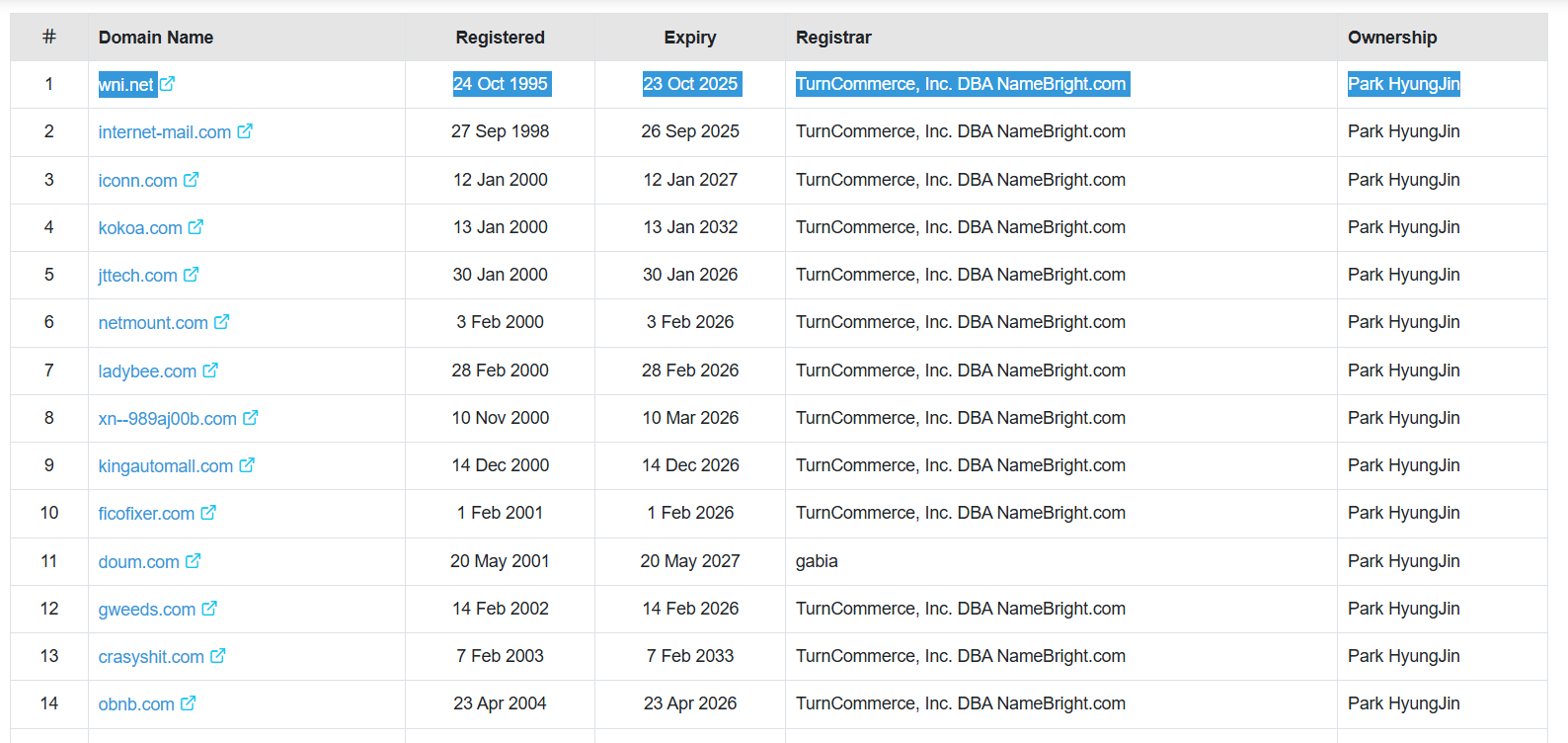
NOTE: You can also find it here but there is no guarantee the this is the oldest one, the records aren’t in order
Last part, we need to find numeric count of leaks that his email appeared in , so we open HIBP and search with his email b2c@naver.com, the result is `4.
For the Bounus part, we go to BreachDirectory and search for the email b2c@naver.com, we get this result:
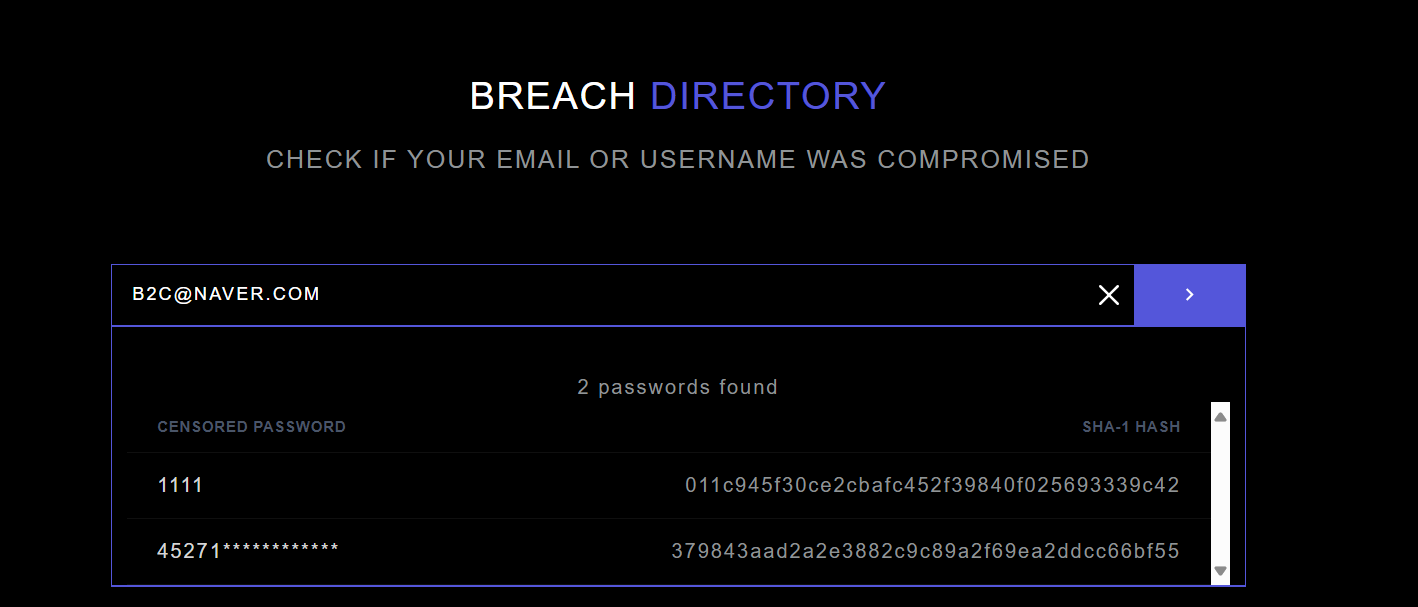
Now we already have the first password 1111. To get the other one we open any hash cracker and select the sha1 algorithm and we get the second password:

NOTE: you can also use this tg bot made by Kalawy to get the passwords straightforward.
Flag: IEEE{Park_HyungJin,wni.net,4}
Bounus: 1111,379843aad2a2e3882c9c89a2f69ea2ddcc66bf55
KA-SAT
Description
In the dawn fog before battle, a pure evil rose, an evil that will touch the sky, the
KA-SAThad been compromised, What began as legitimate commands became a destructive wiper.Investigate this breach using your OSINT and Threat-Intel skills.
Flag Parts:
- Consumer brand of the affected service.
- The group responsible for the attack.
- CRC32-b hash of the only string this wiper writes.
- CRC32-b hash of all 8 targeted paths within the binary (comma separated, in the same order within the binary).
NOTE: if the paths were:
/usr/bin/,/usr/sbin,/usr/tmp, then the hash will be:CRC32(“/usr/bin/,/usr/sbin,/usr/tmp”)
Flag Format:
IEEE{name,group,string_crc32,paths_crc32}
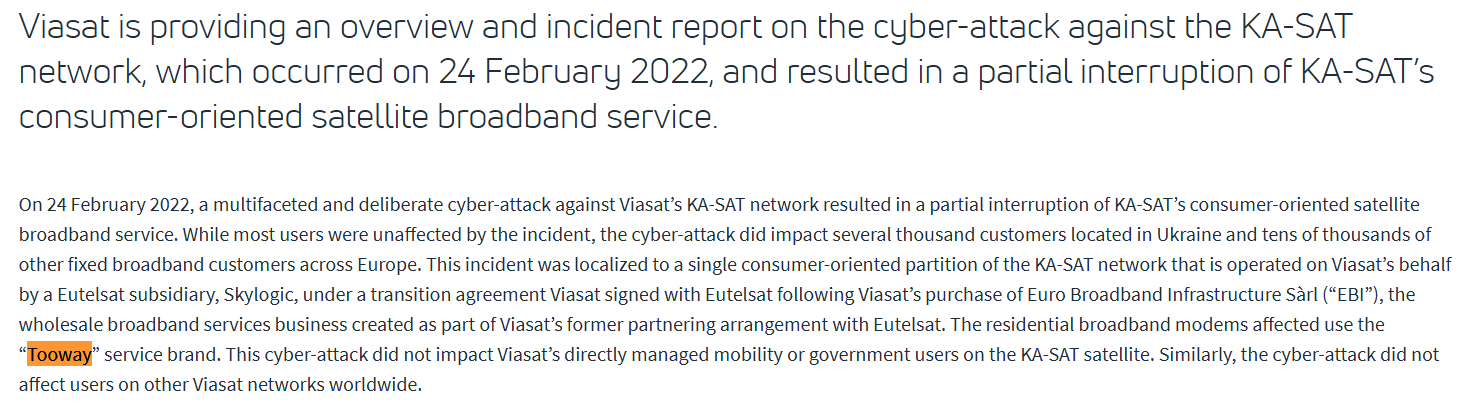
First, a simple search will bring us to the official incident report from Viasat, the owner of the satellite, Now we know what was the incident.
Within the report we find the Consumer brand of the affected service mentioned here:
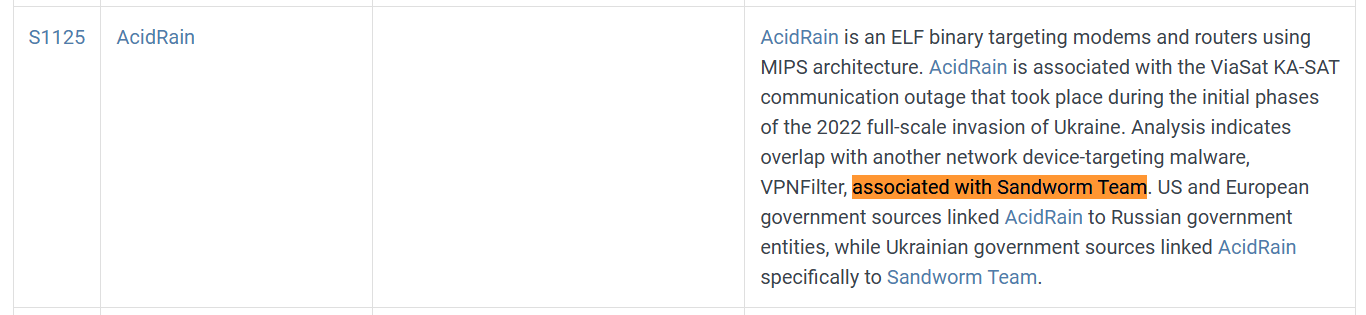
Now, we go to the MITRE ATT&CK software page and search for the incident, we can find it here with the name of the group SandWorm and also the wiper name AcidRain.
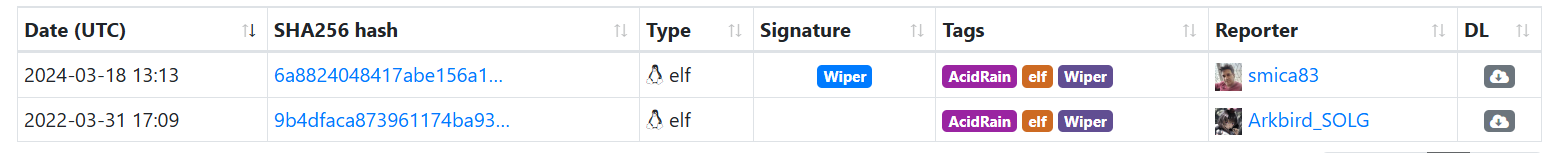
After knowing the wiper’s name we can go to Malware Bazaar and search with the tag AcidRain, we see two samples, we download the oldest one matching the attack date and start analyzing.
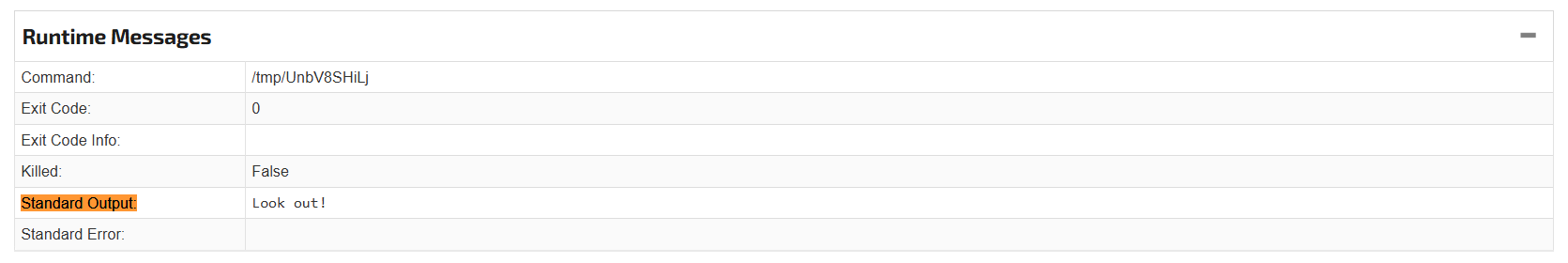
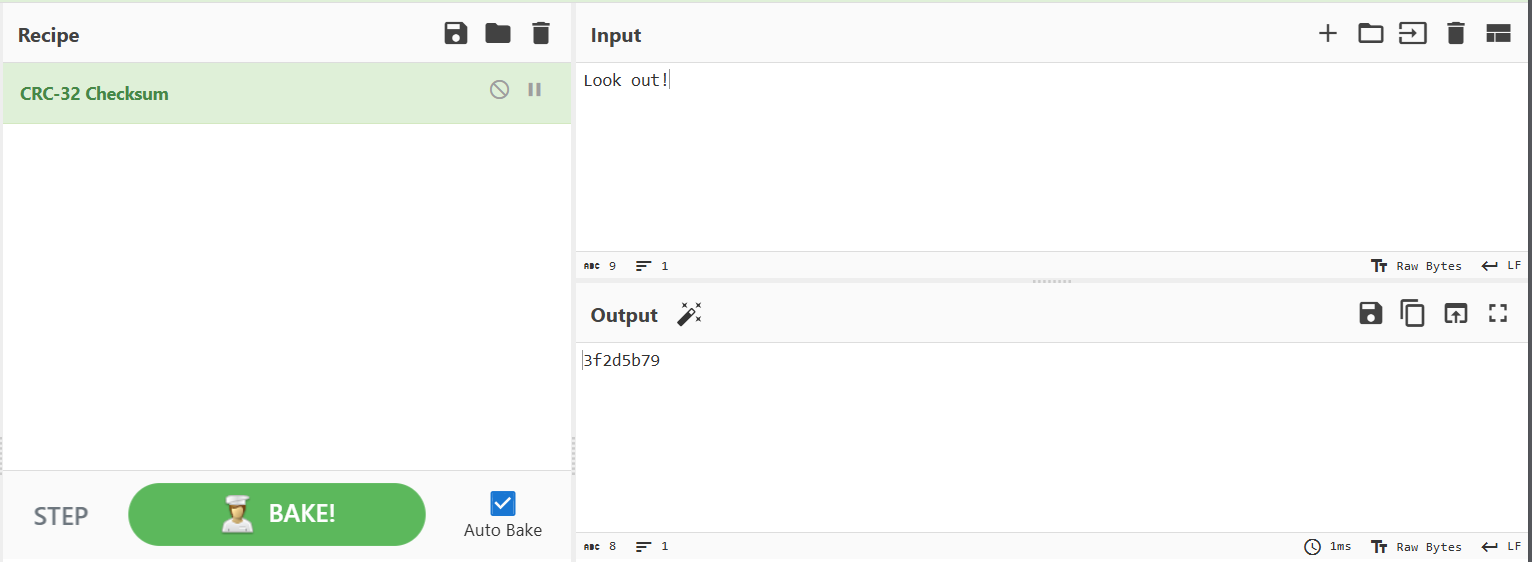
Submitting the sample to Joe Sandbox, we can find the only string printed by searching the Standard Output field.
Using CyberChef with CRC-32, we get our third part of the flag 3f2d5b79
For the last part, according to Sentinel Labs report, the targeted paths are hardcoded within the binary making it easy for an in-depth wipe of the filesystem and various known storage device files, so we only need to run strings on the binary to get them in order.
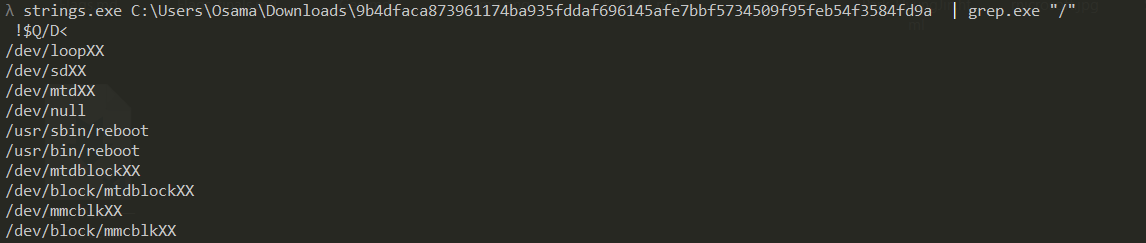
Now we have them:
- /dev/loopXX
- /dev/sdXX
- /dev/mtdXX
- /dev/mtdblockXX
- /dev/block/mtdblockXX
- /dev/mmcblkXX
- /dev/block/mmcblkXX
NOTE: in the description, I asked for 8 targeted paths, there are only 7; I mistakenly counted /dev/null as a targeted path.
So now, we format them as the description said, and we get this hash a05e040f
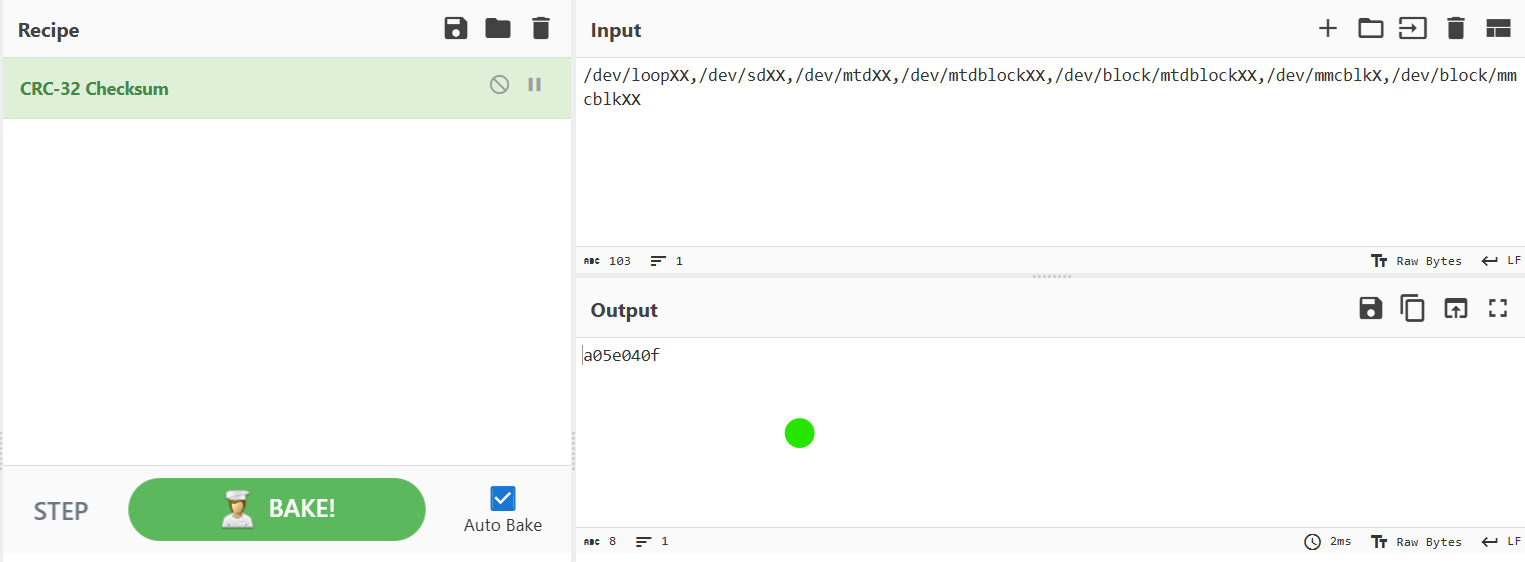
Flag: IEEE{Tooway,Sandworm,be408ebe,a05e040f}
Sport
Description
Nothing beats a good sports time. Find where I’m and the next match will be on me. Provide the coordinates of the place rounded to 3 decimal places.
Flag format: IEEE{LAT,LON}
Example: IEEE{36.806,10.181}

First with some image-searching and comparing similar images, the construction style strongly suggests this place is in عين السبع بالمغرب.
We notice that there is a banner hanged on the playground wall’s net, It has some Arabic words but we cann’t read it clearly, this is a strong identication that Morocco is correct

After some edit to the image and giving it to any AI agent, we can conclude that the phrase is الفضاء الرياضي إقامة الشباب, so we search on it on the maps and start search for any playgrounds in the found area till we find this:
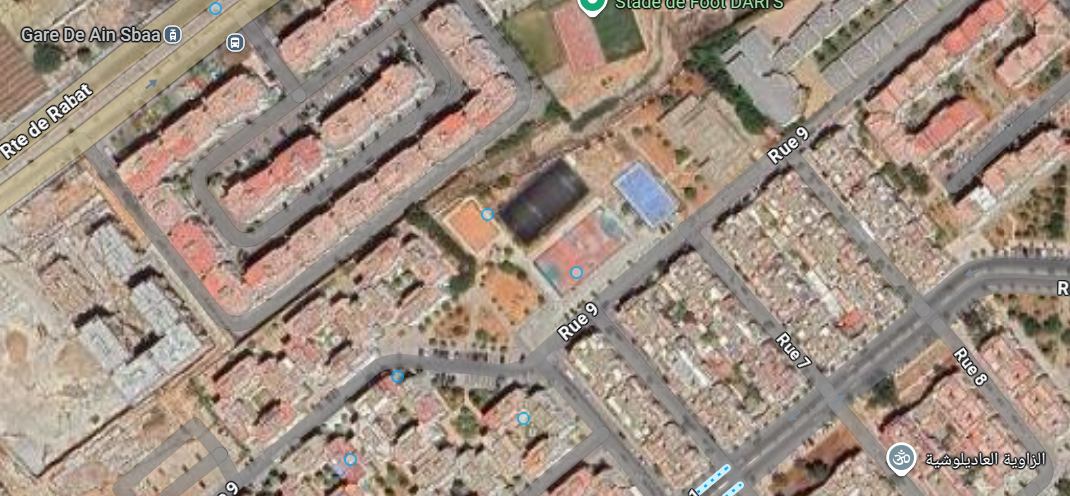
Opening the street view, we get these two images:
This is our place.
Flag: IEEE{33.607,-7.523}
THE END
