DUNE - OSINT Writeup
Description
In the world of Dune, everything has two faces depending on who you are.
A Fremen can be a trusted ally to House Atreides… or a nightmare to House Harkonnen.
In the last cycles, our largest automation colony, Arrakis-colony, was hit by a so-called Sand Worm.
The harvesters stalled, telemetry went wild and, worst of all, Secrets were stolen.
Your mission is to help us understand what really happened – and recover what was taken.
Find our official Presence on the Open Web.
From there, track down where we keep our harvesters’ Source Code.
Somewhere in those spice Packages you will see what the sand beast did to us.
Rumours say that someone has already seen a piece of our secrets and left traces of it behind.
We need you to confirm or deny this, and follow the trail as it moves across dunes.
Be aware of the Many Fakes, If you read the signs correctly and follow every breadcrumb, you’ll uncover all stolen fragments.
Flag format
The recovered secret is split into three parts:
> 0xL4ugh{part-1part-2part-3}
(no spaces).
Keywords
From the description, we find some interesting keywords:
Arrakis-Colony
Sand Worm
Secrets were stolen
Presence on the Open Web
Source Code
Packages
Many Fakes
Trying some steganography on the description, the Zero-Width Characters results in the following flag:
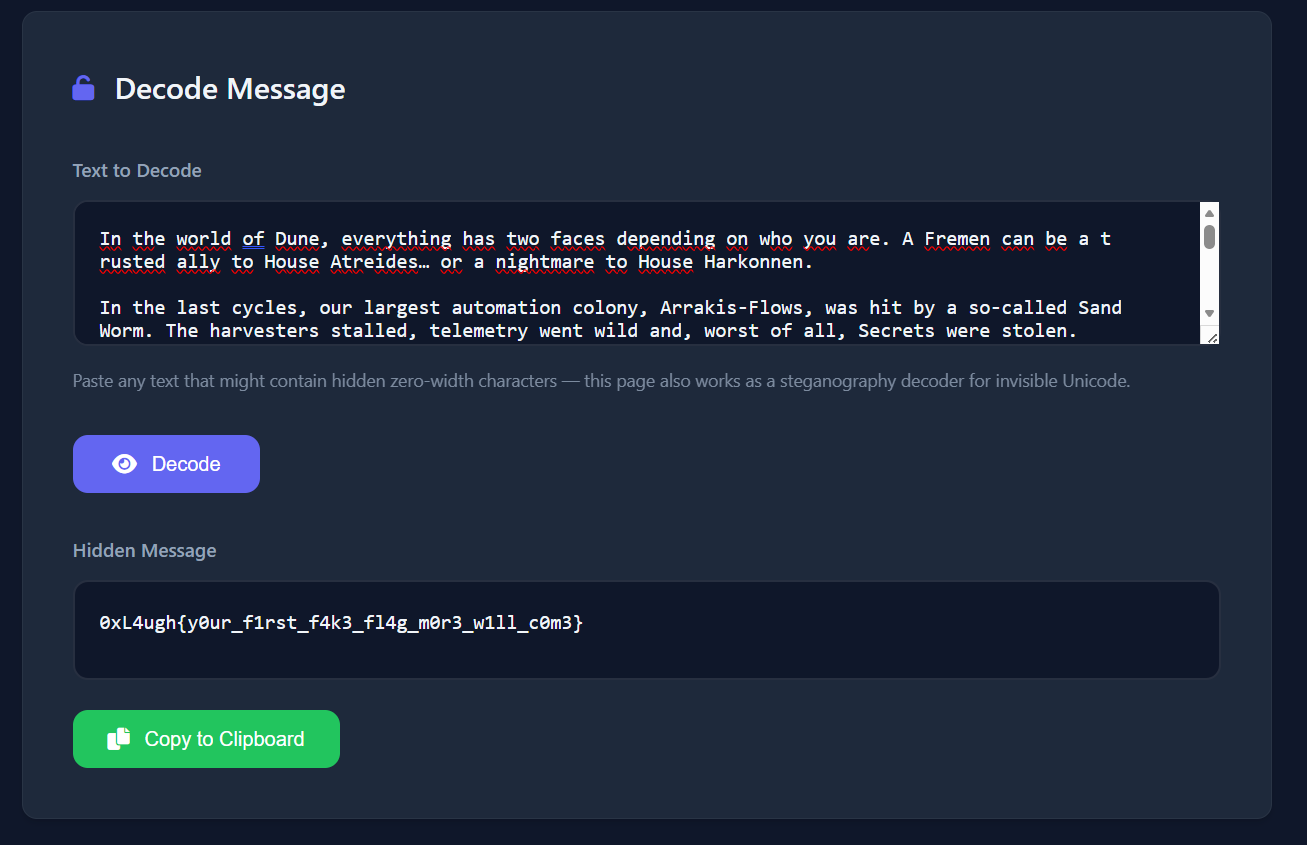
This flag is the first of almost 14 fake flags distributed across different areas throughout the whole challenge to prevent rabbit-holes and make you stick to the desired path, so if you found one, that means you took a wrong turn, take a step back and think smarter.
Web Fragments
From those keywords, we start searching the open web for any presence of Arrakis-Colony, I used multiple search dorks on different browsers, including bing, yandex, Google, yahoo and even DuckDuckGo, I used dorks like:
- "Arrakis-colony"
- "Arrakis colony" "Packages"
- "Sand Worm" "0xL4ugh-CTF"
- ...
there was absolutely nothing until this dork worked on Google:
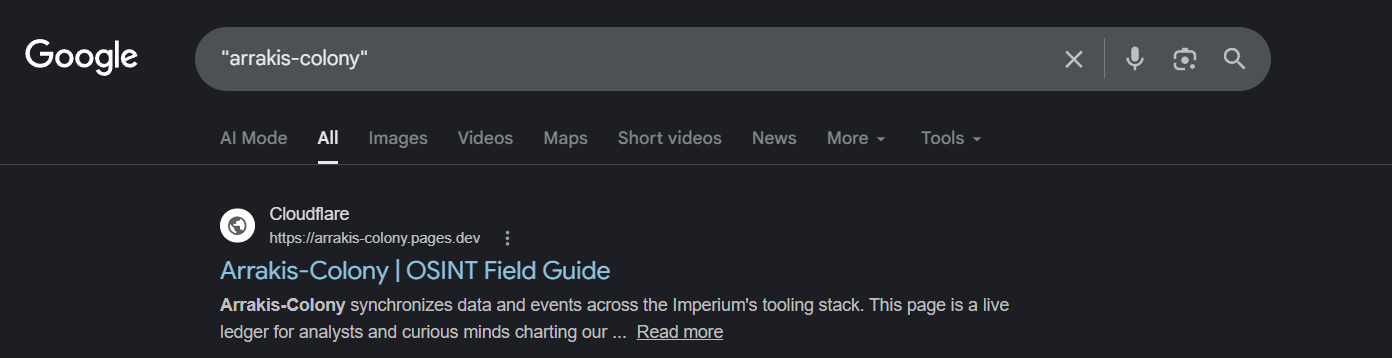
The website is intentionally configured so that only Google indexes it reliably, other search engines either don’t index it or are very slow to pick it up.
Now that we have the Arrakis-Colony’s official presence on the Open Web, we search the whole website til we find the contact-us section which has links for GitHub, LinkedIn and Telegram, the keywords had Source Code andPackages so we start with GitHub.
GitHub
Viewing the repositories, we see that there are 5 repos, 3 NPM packages and 2 odd repos.
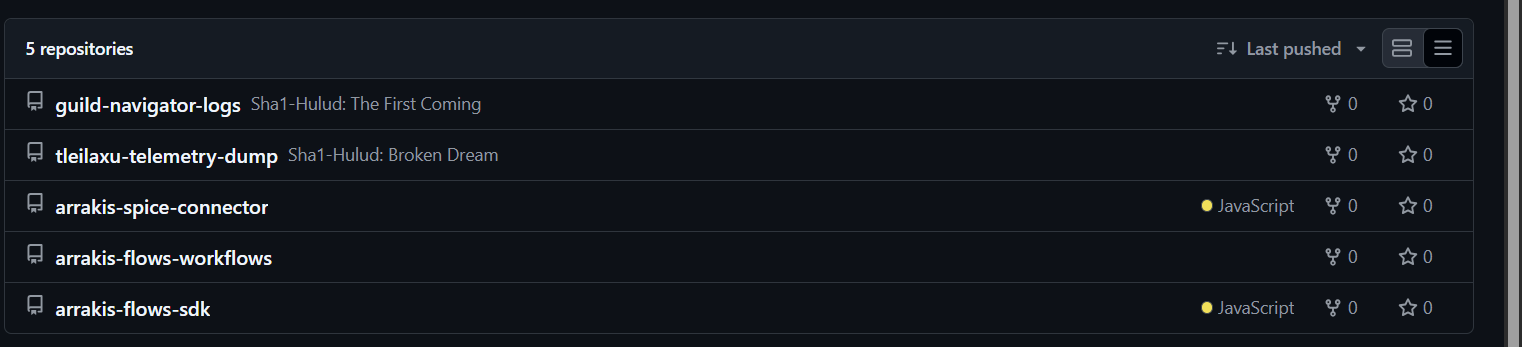
Further investigation shows odd commits in arrakis-spice-connector repo, two files were added.
package.js which uses postinstall to install setup_spice_telemetry.js, which does some odd loggings staff.
After some search we find out that this is very similar to the recent Shai Hulud 2.0 Supply-Chain Attack that took place in November 24 this year.
Based on this report, the Shai Hulud is a worm that installs bun with the file setup_bun.js and then uses that to execute bun_environment.js which is the actual malicious code then creates a randomly named repository with stolen data
the malware also publishes secrets to GitHub, with a random name and the repository description: Sha1-Hulud: The Second Coming.
So, the repo arrakis-spice-connector is infected with the shai hulud worm, this is what the challenge description meant by Sand-worm/Sand-beast, this also explains the previous 2 odd repos, they were generated by the worm. but the odd thing is that the worm usually makes repos with the description Sha1-Hulud: The Second Coming. when successful, but that didn’t happen here, we have Sha1-Hulud: Broken Dream and Sha1-Hulud: The First Coming but no Sha1-Hulud: The Second Coming., also the setup_spice_telemetry.js code has this:
log("Archive route: github.com/arrakis-flows/sietch-secrets-archive");
log("Echo hint: Second dream of Arrakis.");
But this repo doesn’t exist!
The description says that someone has already seen a piece of our secrets and left traces of it behind
Web Archive
By checking common web archives like archive.is and the Wayback Machine for any traces of the missing repo we find this snapshot, which indicates the previous existence of the desired repo.
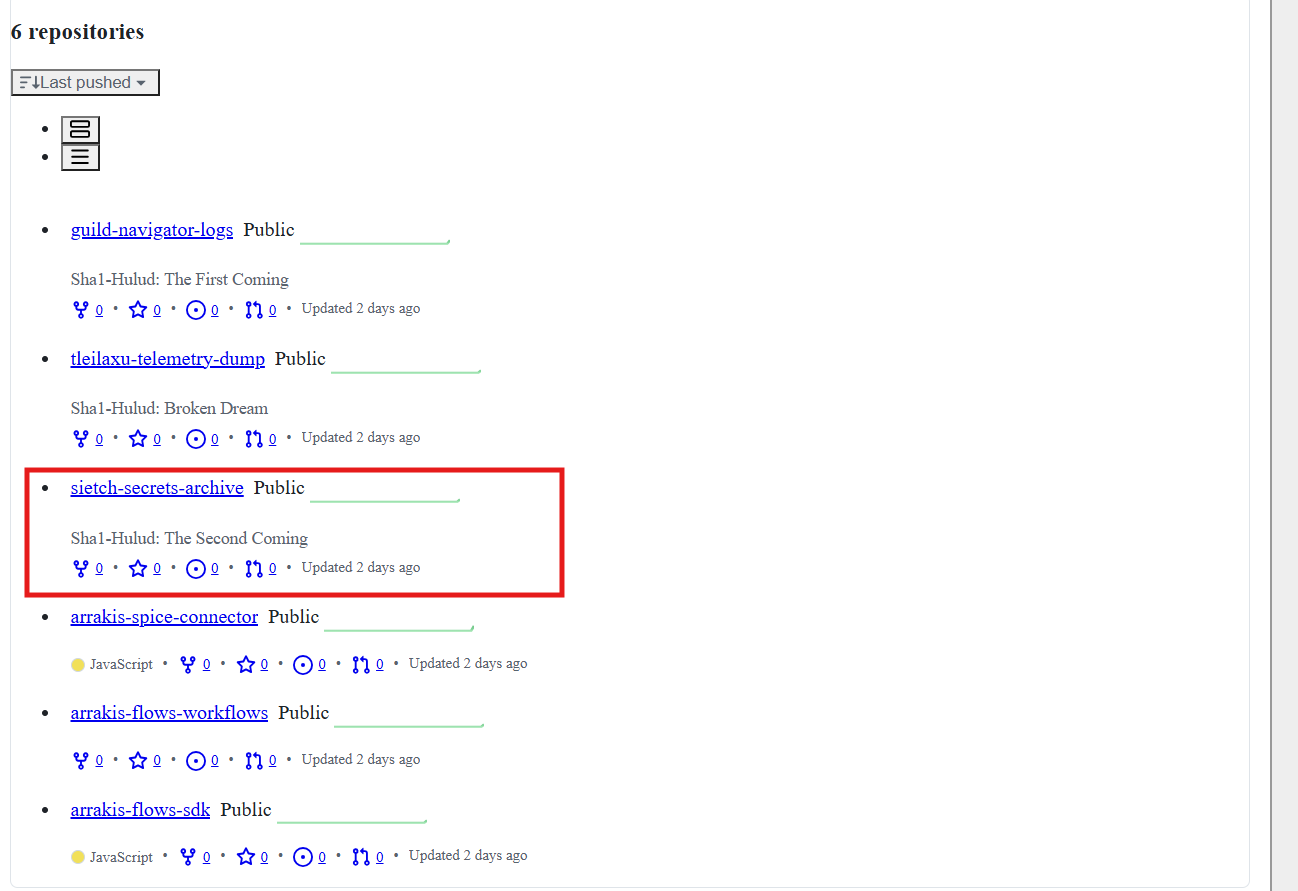
Maybe these guild-navigator-logs and tleilaxu-telemetry-dump repos were failed tries and the sietch-secrets-archive was the successful one.
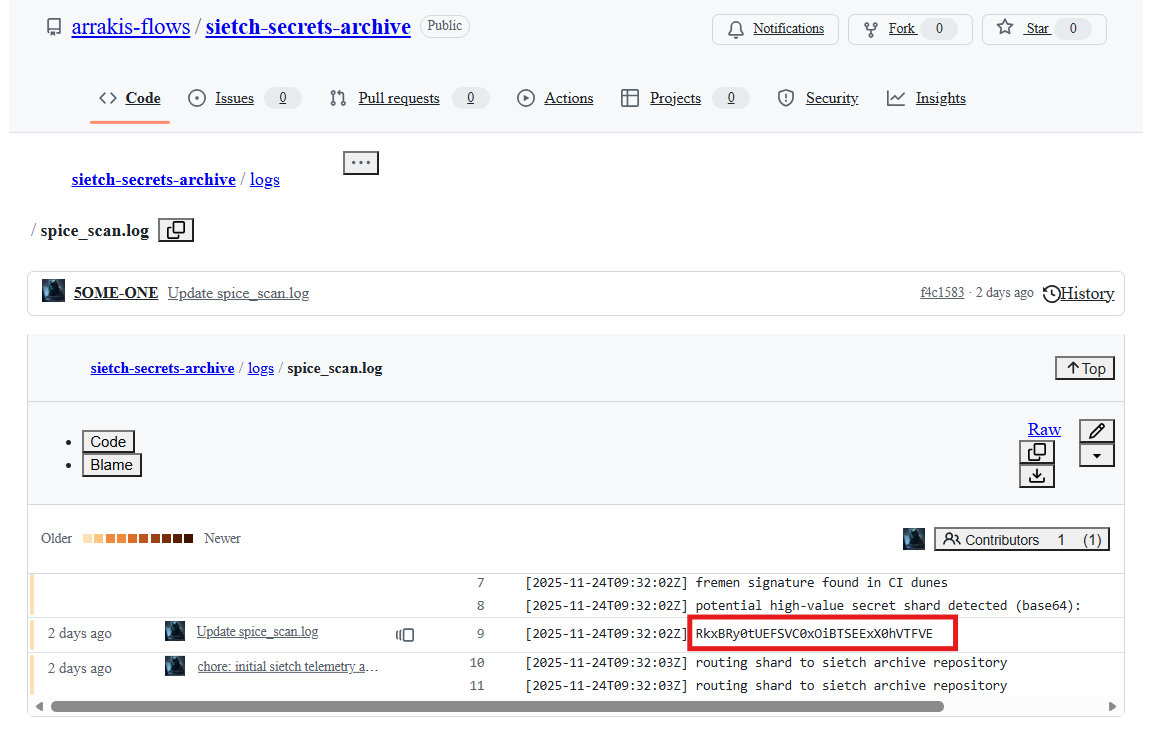
We search for any other snapshots for this directory using wildcards to find another 3 snapshots, one of them has this path within the repo
sietch-secrets-archive/blame/main/logs/spice_scan.log
opening it, we see this:
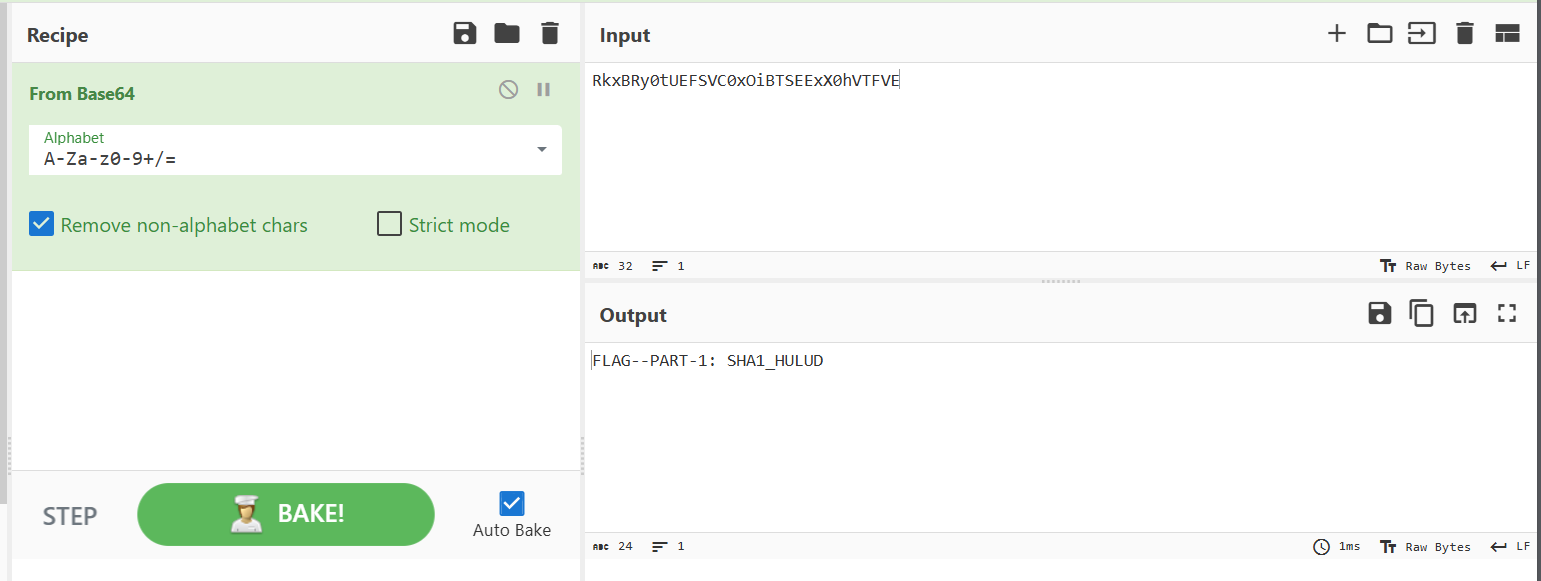
Decrypting it using cyberchef
Back to Beginning
Since we already pulled everything GitHub-related, we take a step back to the website, we get back to contact us section and go for the LinkedIn page, we see only one post there:
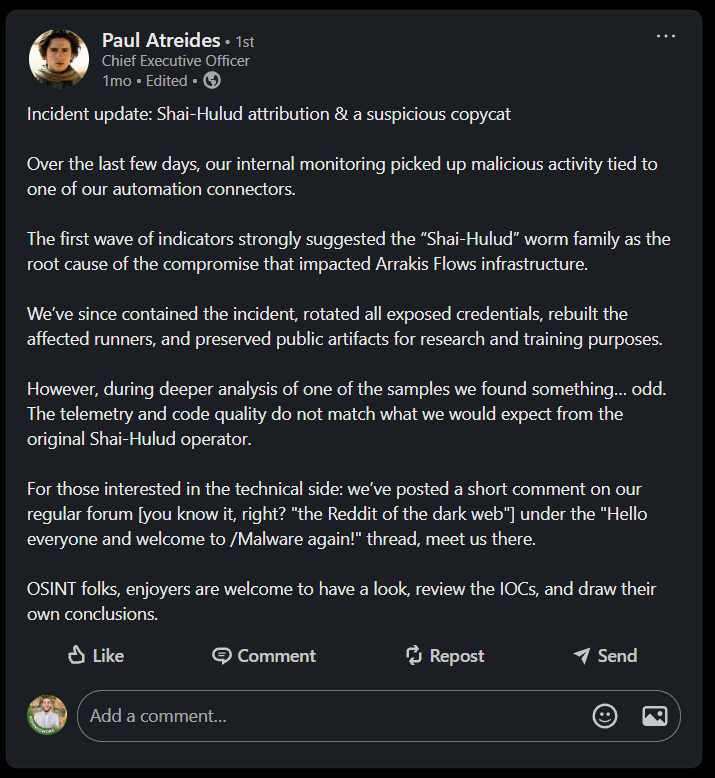
Reddit of the Dark Web
We need to find that thread, we search for that Reddit of the dark web forum to find out that it’s actually Dread, so we setup our Tor browser and go there searching for it.
After some searching, we encounter this comment on the mentioned thread:
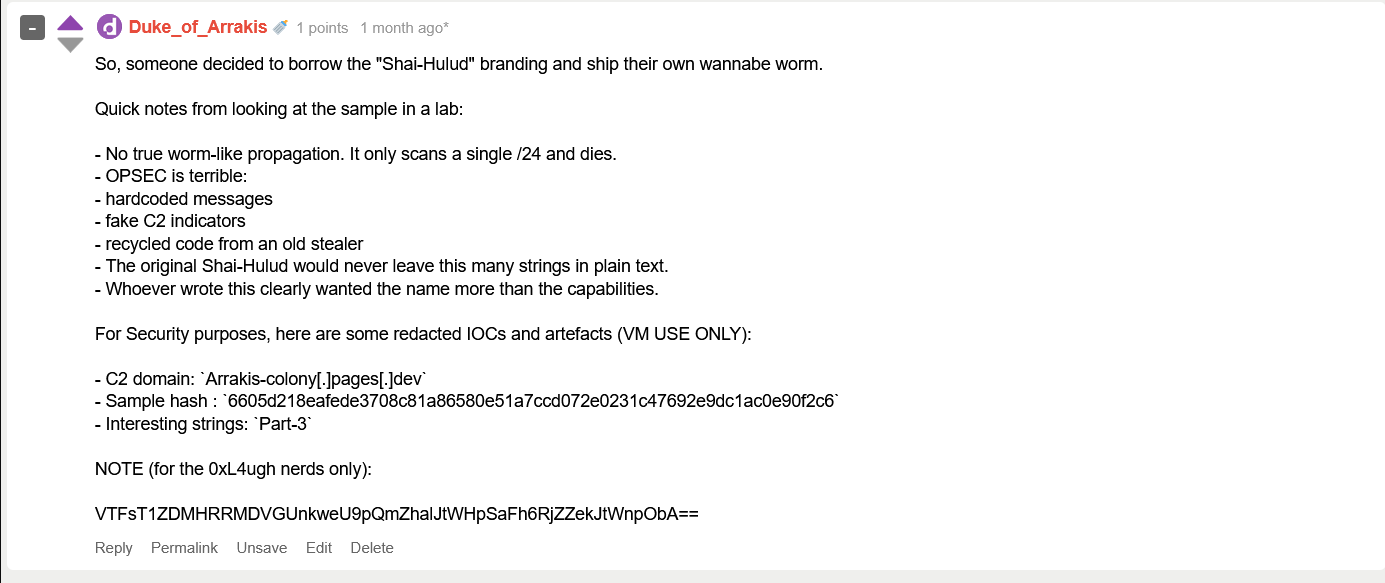
Useless Note
ㄟ( ▔, ▔ )ㄏThe thread is posted by
Duke_of_Arrakiswho isPaul Atriedesif you’re a fan of the dune worldBut that doesn’t change anything.
Using cyberchef again to decrypt the second part will result in:
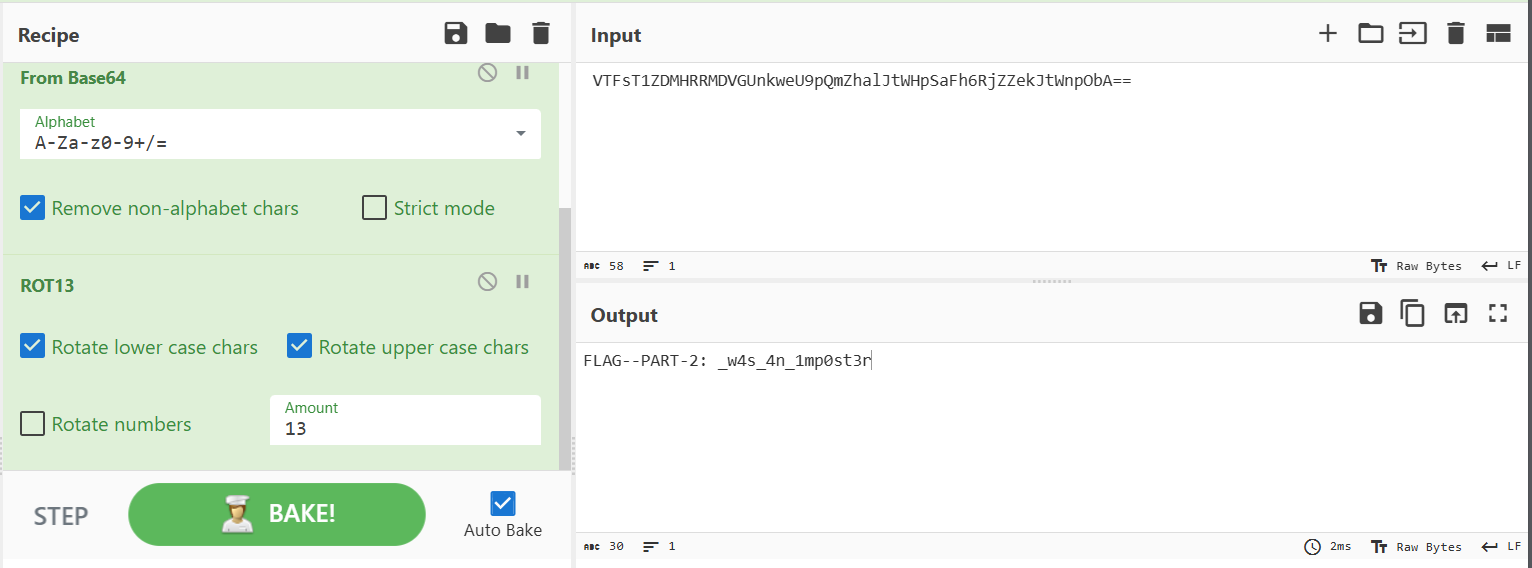
Sample Hunting
From the previous thread, we found some IOCs for a sample, the sample contained the string Part-3 indicating that it has the rest of the flag.
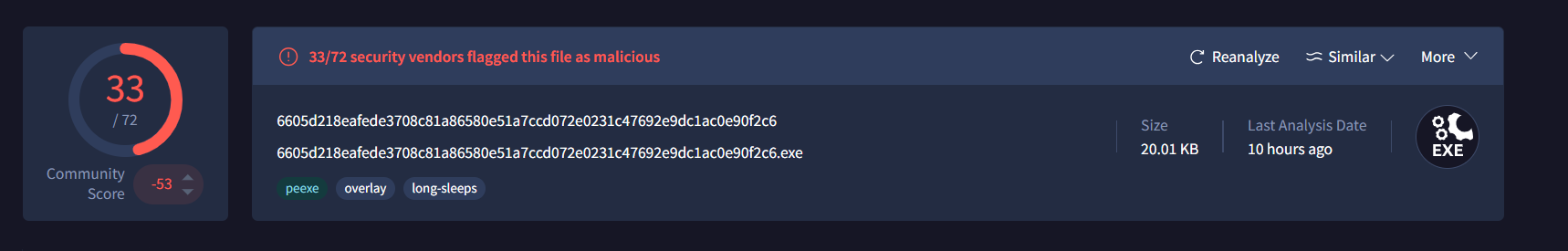
Searching with the hash on MalwareBazaar will result in this sample, which has the following tags indicating it’s our desired sample.
The sample is intentionally crafted for this CTF, it is flagged as malware on VT and similar services for realism.
Still, handle it in a VM.
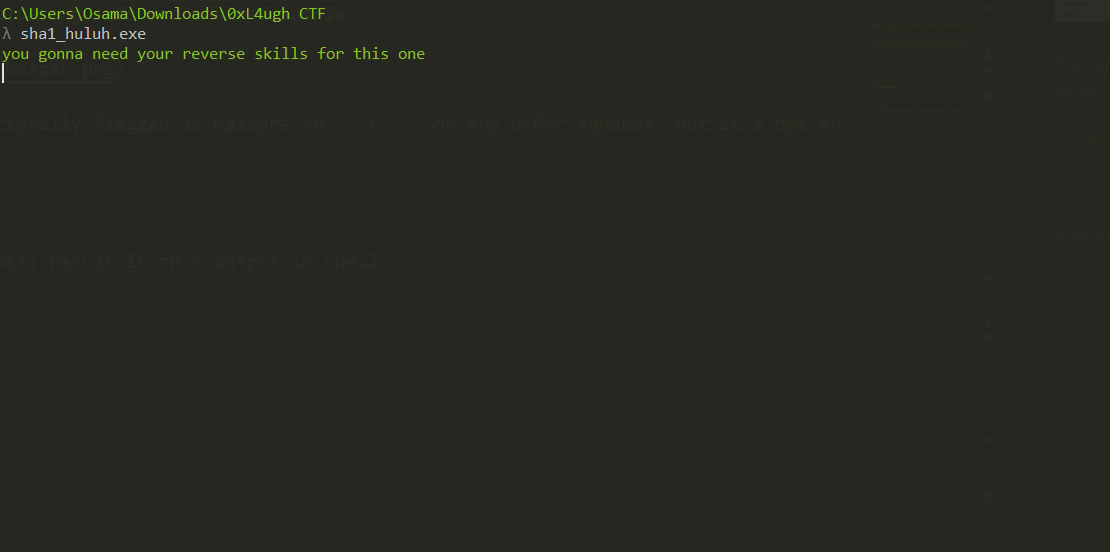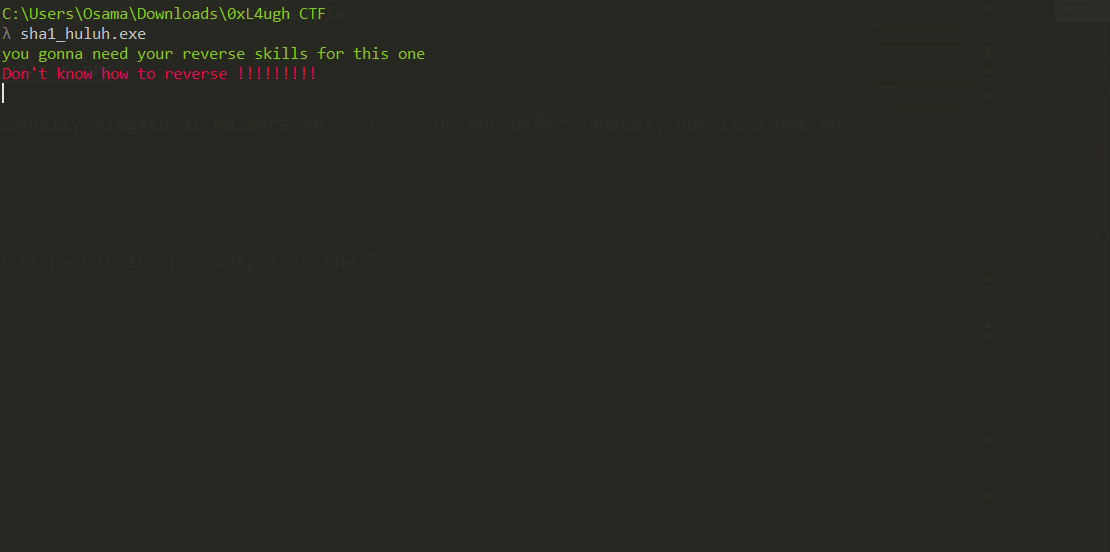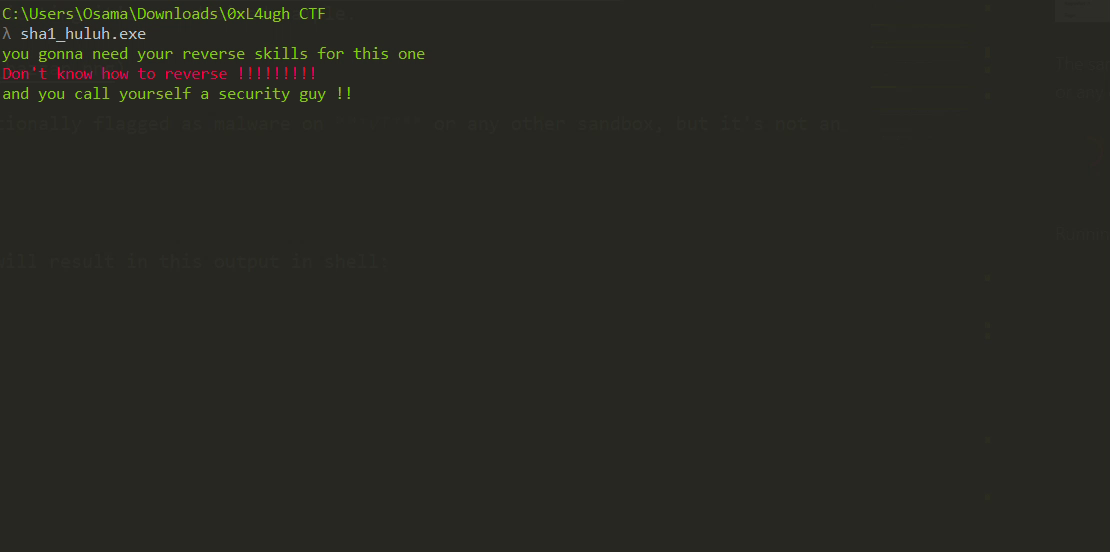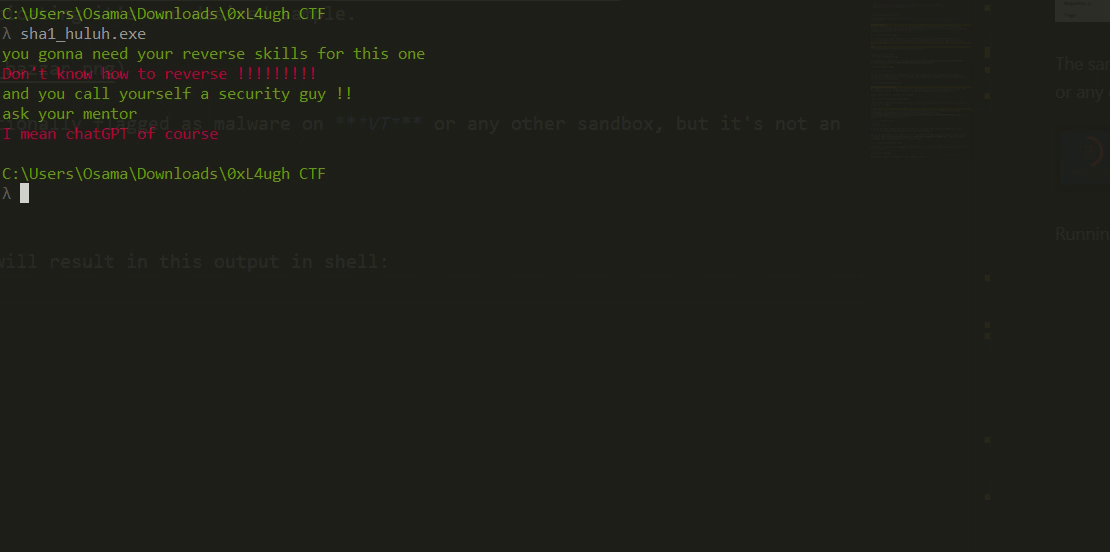
Running the sample will result in this output in the shell before deleting itself:
Do We Need Reversing?
Actually no, you can just upload the sample to any sandbox and see what it does or search for the string Part-3:
But this is not what I would do.
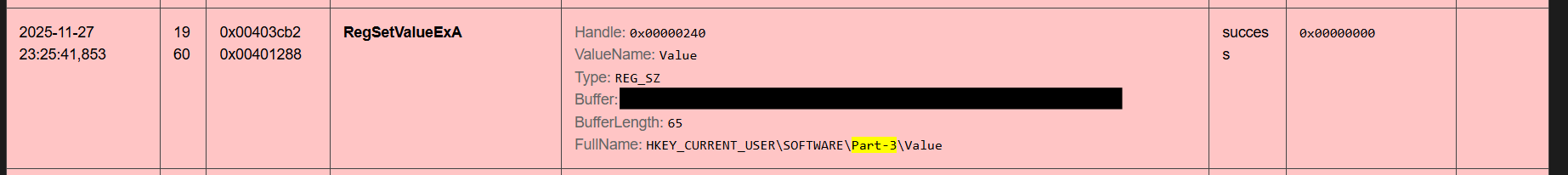
This means it’s IDA time; I opened the strings tab then tracked where the Part-3 string was used in the decompiled code; it was RegCreateKeyExA followed by RegSetValueExA and RegCloseKey, so we put a breakpoint there and inspect the value in the ‘string’ variable.
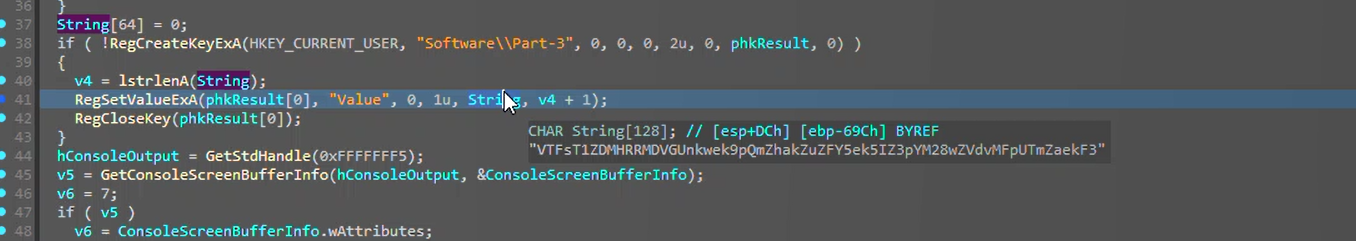
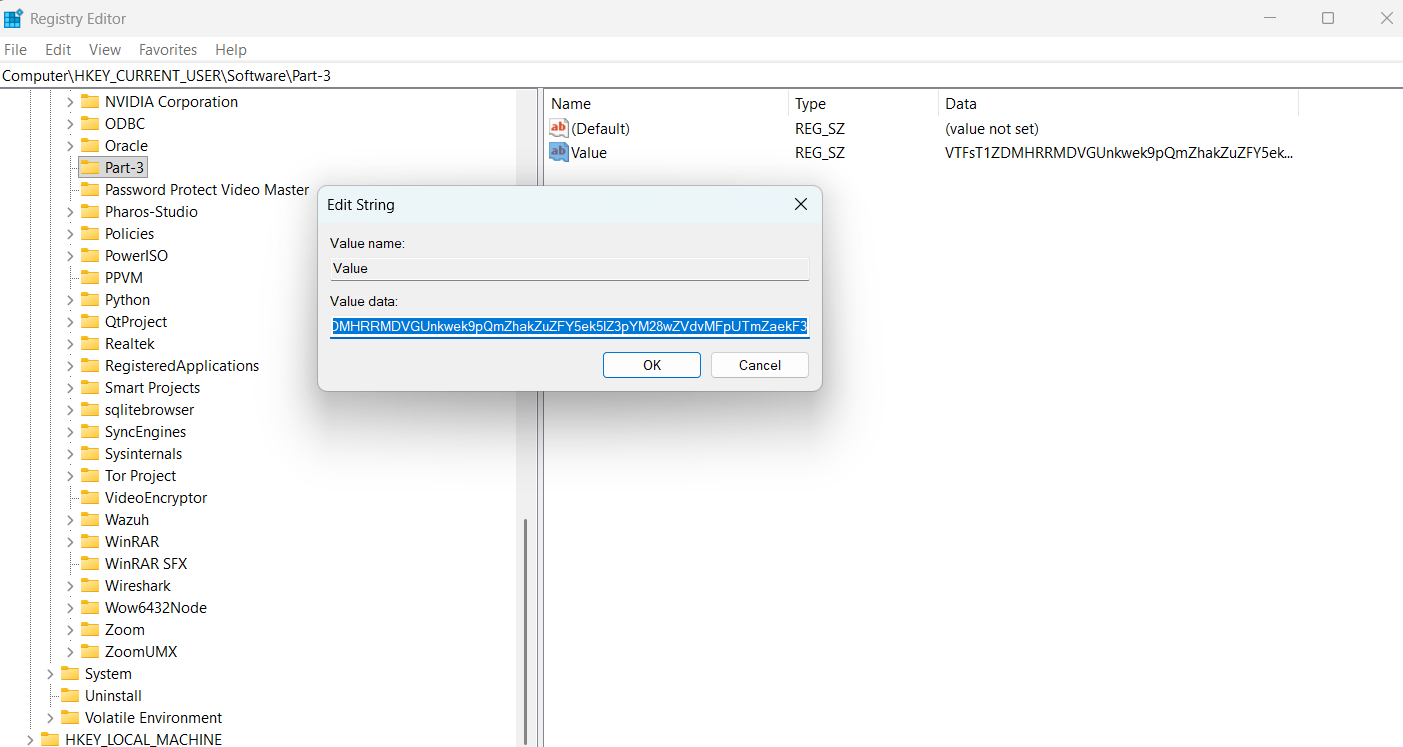
Verifying this in regedit will result in this:
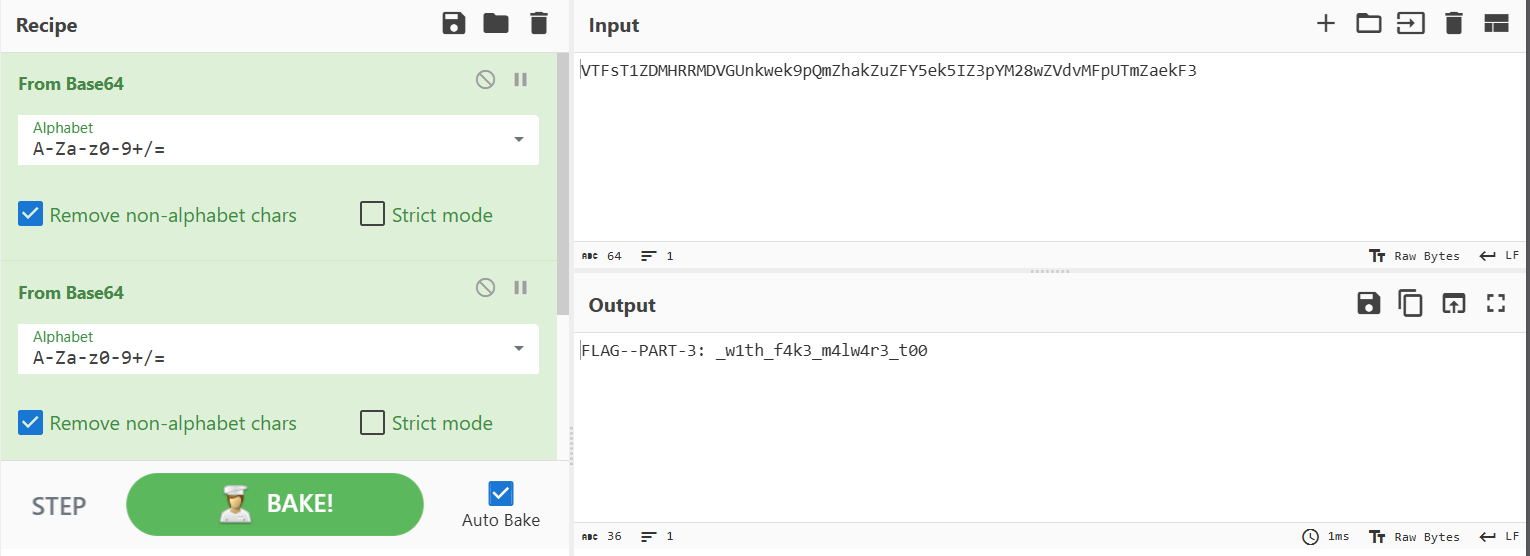
Back to cyberchef again to decode the last part:
Full Flag
0xL4ugh{SHA1_HULUD_w4s_4n_1mp0st3r_w1th_f4k3_m4lw4r3_t00}
What we really learned?
-
Not everything archived in wayback machine, you can always find solid data in other archives as well.
-
Understanding search queries for dark forums like
Dreadis a must for any real OSINTer [the hint made it too easy for you]. -
Threat-Intel platforms are always useful for real-case scenarios.
Conclusion
At the end, I hope you have learned something from this challenge and had some fun.
I also hope you didn’t curse my name for all those fake flags ¯\_(ツ)_/¯
THE END