Chapter-7 PMA Write-up
Lab 7-1 :
Analyze the malware found in the file Lab07-01.exe.
Q1: How does this program ensure that it continues running (achieves persistence) when the computer is restarted?
Answer :
By checking the main function using IDA-PRO, we see that a hint
says MalService then a call to StartServiceCtrIDispatcherA function.
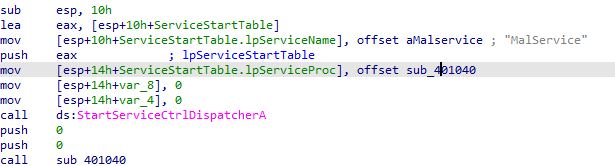
By getting into the sub_401040 we see evidence of creating a service.
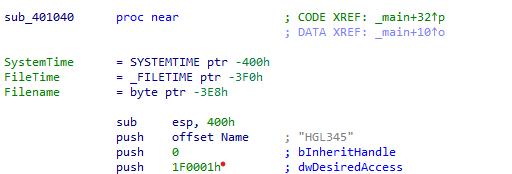
According to the MSDN page the StartServiceCtrIDispatcherA actually connects the main thread of a service process to the service control manager, which causes the thread to be the service control dispatcher thread for the calling process, Now we know for sur it creates a service.
Q2: Why does this program use a mutex?
Answer :
We continue to see that it calls OpenMutexA to open a mutex called HGL345 then tests the returning value.
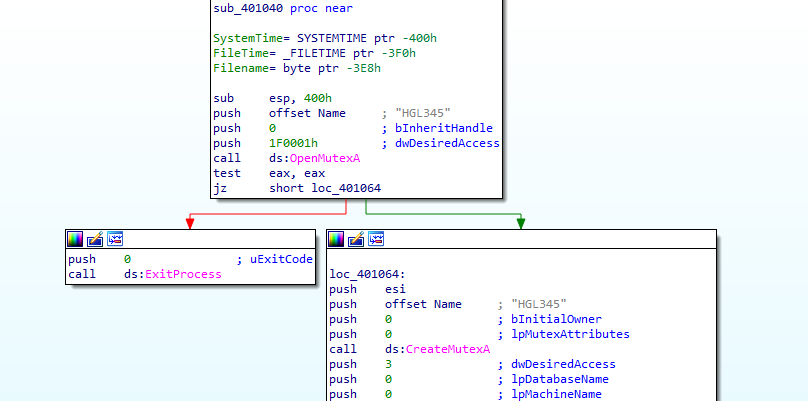
depending on the result of the test, the program will either terminate or jump to loc_401064 which will create a mutex under the name of HGL345.
This technic is used to make sure that there is only one piece of the malware runing on the machine.
Q3: What is a good host-based signature to use for detecting this program?
Answer :
The best way to detecte that malware is bt searching for a mutex named HGL345 or a service named MalService.
Q4: What is a good network-based signature for detecting this malware?
Answer :
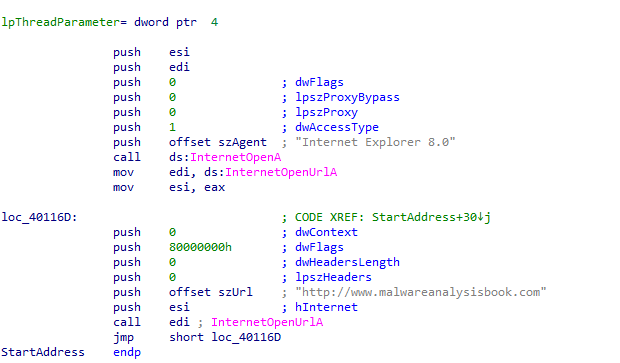
Now we see that it uses the user-agent Internet Explorer 8.0 to get access to the url http://www.malwareanalysisbook.com which represent a network-based indicator.
Q5: What is the purpose of this program?
Answer :
The purpose of this program could be obtained from the next:
-
At loc_401064 we can see that the malware is setting a timer to
834hwhich is2100in decimal.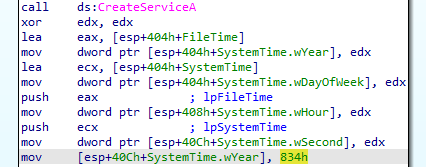
-
Next malware is set to sleep untill the year of 2100 comes.
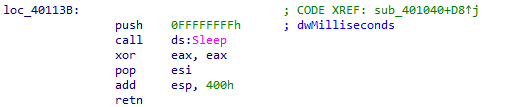
-
When that year comes, an infinte loop will start sending requests to the url
http://www.malwareanalysisbook.comas a distributed denial-of-service (DDoS) attack.
Q6: When will this program finish executing?
Answer :
This program will never terminate as it is uncodditional jump to an INFINITE LOOP.
Lab 7-2 :
Analyze the malware found in the file Lab07-02.exe.
Q1: How does this program achieve persistence?
Answer :
While examining the program we found no evidence of achieving persistence, there is no creation for any scheduled tasks, services, startup files, or run keys.
Q2: What is the purpose of this program?
Answer :
- By diging into the program we can see a
OleInitializeandCoCreateInstancefunctions which are used to initialize a COM object and set its defalut values to a specified CLSID. -
Then, we see a call to “VariantInit” function to intialize a string to
http://www.malwareanalysisbook.com/ad.html. -
Then it excutes that string with the created COM object (likely Internet Explorer).
-
The program will free this string lately after excutes it.
- In total, this program is creating a COM object and uses it to open a URL that may be an advertisement as it ends with
ad.html(We can make sure of that by running the program).
Q3: When will this program finish executing?
Answer :
The program will finish excution whe the ad already appears.
Lab 7-3 :
For this lab, we obtained the malicious executable, Lab07-03.exe, and DLL, Lab07-03.dll, prior to executing. This is important to note because the malware might change once it runs. Both files were found in the same directory on the victim machine. If you run the program, you should ensure that both files are in the same directory on the analysis machine. A visible IP string beginning with 127 (a loopback address) connects to the local machine. (In the real version of this malware, this address connects to a remote machine, but we’ve set it to connect to localhost to protect you.)
WARNING
This lab may cause considerable damage to your computer and may be difficult to remove once installed. Do not run this file without a virtual machine with a snapshot
taken prior to execution.
This lab may be a bit more challenging than previous ones. You’ll need to use a combination of static and dynamic methods, and focus on the big picture in order to avoid getting bogged down by the details.
Q1: How does this program achieves persistence to ensure that it continues running when the computer is restarted?
Answer :
By looking to the program we can’t see any obvious proof of persistance, but there is alot of suspicious things within the file that could be described as next :
-
First, we see a reference to the supplied DLL
Lab07-03.dlland the windows DLLKernel32.dll.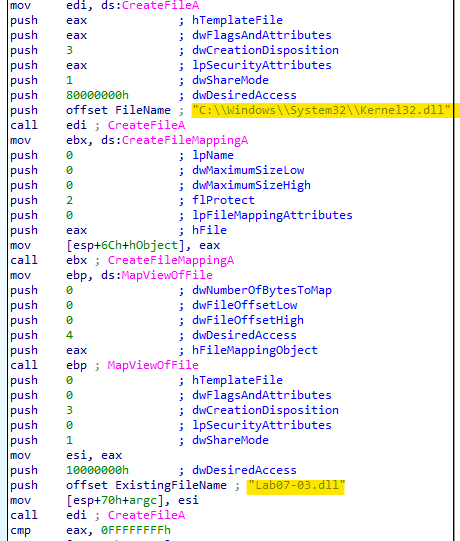
-
Second, we see reference to pushing a close-label but different dll under the name of
kerne132.dll.and the supplied dllLab07-03.dllonto pathC:\\windows\\system32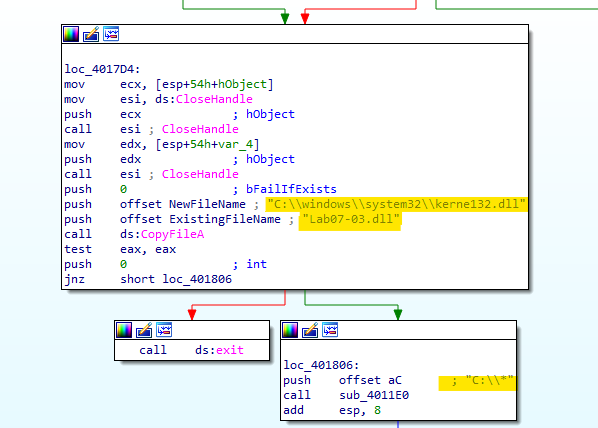
-
Then, we see a call to “sub_4011E0” which is doing a search for every file in the
C:\\*directory.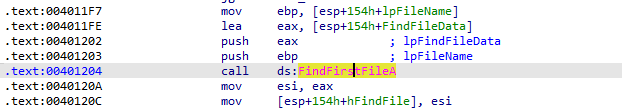
- Now we can see alot of chaos like jumps and comparisions, but that’s not our concern right now.
-
By continue searching, we can see a comparison occurs that checks if a file is a .exe and if it is, it calls the “sub_4010A0”.
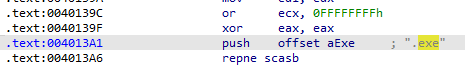
-
In “sub_4010A0” we see a call to 3 functions
CreateFile,CreateFileMapping, andMapViewOfFile, these fuctions are typically used to map a file to memory and modify it.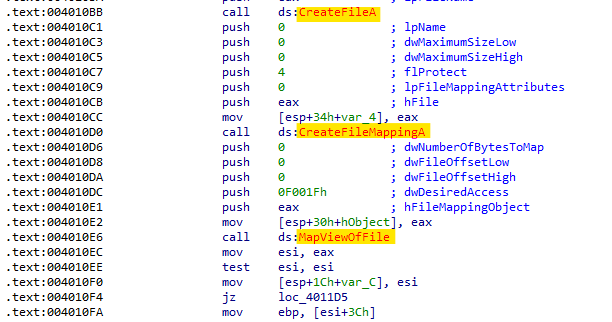
-
After mapping the file into memory, we see a comparison between
kernel32and a loction in the exe file, if it’s found it copies a value referenced by “dword_403010” over the top of it.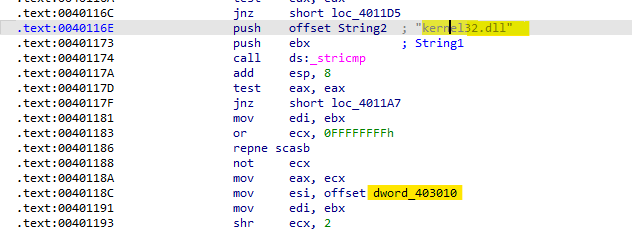
-
the value stored in the “dword_403010” is
6E72656Bh, by converting it to an ASCII string we see it’s actual value.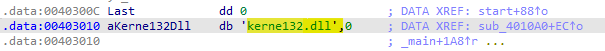
In brief, this program searches for all .exe files within C Directory, when an exe is found, it loads it into memory and replace the kernel32.dll with kerne132.dll, this is the way it gains persistance.
Q2: What are two good host-based signatures for this malware?
Answer :
The best two host-base indecators are :
-
The first is writing the DLL
kerne132.dlltoC:\Windows\System32and modifying every .exe file on the system to import that DLL instead of the original onekernel32.dllas we described previously.(Note, it uses number 1 instead of letter L).
-
We can the second on inside the “Lab07-03.dll”, a creation of mutex under the name of
SADFHUHF.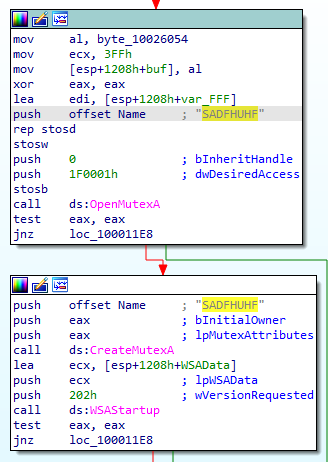
Q3: What is the purpose of this program?
Answer :
-
According to Q1, this is an advenced back-door that makes a remote access connection.
-
By analyzing Lab07-03.dll, we can see the connection is set with IP 127.26.152.13
-
the prgram has a lopp to choose between two cammands, either sleep or exectue.
Q4: How could you remove this malware once it is installed?
Answer :
-
To remove this malware you can write a script or a program to undo all changes to the executables.
-
Another handy and tricky way is to just delete the
kerne132,dlland rename the windowskernel32.dllto the deleted one.
Be Carefule while doing that, because the system may crash during booting due to no variant of kernel32.dll being present.
THE END